Widespread Exploitation Continues: MOVEit CVE-2023-34362 Leaves Organizations at Risk

MOVEit CVE-2023-34362 is a Critical SQL Injection vulnerability rated 9.8. It affects all versions of Progress Software’s managed file transfer (MFT) solution, MOVEit Transfer. This vulnerability has the potential to grant unauthorized access. For in-depth information about the vulnerability, including mitigation measures, incident response, and the attack surface, refer to our previous blog post published on June 6th.
Given the ongoing impact of this vulnerability, this blog post aims to provide an update on the developments that have taken place since its discovery.
MOVEit CVE-2023-34362 In The Wild
The vulnerability continues to wreak havoc across organizations. Since our previous blog post, the impact of this vulnerability has escalated, with over 270 organizations affected, resulting in 33 data leaks and impacting more than 1.7 million individuals, according to KonBriefing Research.
It started with CISA confirming that the CL0P Ransomware Gang, also known as TA505 is among the entities responsible. In May 2023, they exploited the vulnerability, and installed a web shell named LEMURLOOT on the MOVEit Transfer web applications which can be connected only with a password.
Researchers at Kroll Threat Intelligence found evidence that the group experimented with ways to exploit the vulnerability since 2021.
Various Organizations, including Universities, Banks, Hospitals, and Toyota, have confirmed being affected by the vulnerability. Additionally, the energy giant Shell has confirmed that personal data belonging to its employees has been leaked.

Diagram usable according to license: Creative Commons BY 4.0, credits: KonBriefing Research
Comparing Results
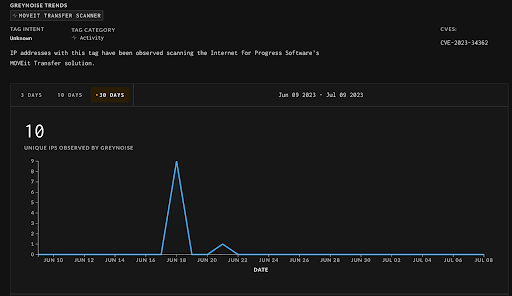
According to GreyNoise results, there are 10 identified IP addresses that have been observed scanning for Progress Software’s MOVEit Transfer in the past 30 days (between June 9 to July 9) which is a great reduction compared to the previous blog which presented 90 identified IP addresses over 3 days (between June 1 to June 4).
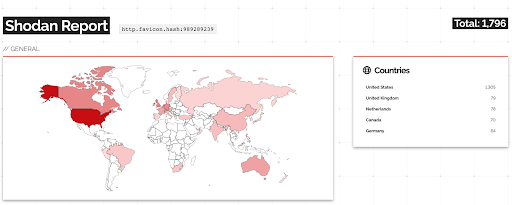
According to Shodan, there are currently over 1,700 publicly-facing MOVEit applications which is also a decrease compared to the previous blog which reported over 2,500 results.
However, this reduction is insufficient, particularly considering the high public visibility of the vulnerability and its known exploitation in the wild.
Recommendations
Users of the following MOVEit versions are advised to patch their system immediately:
- MOVEit Transfer 2023.0.0 upgrade to 2023.0.2 (15.0.2)
- MOVEit Transfer 2022.1.x upgrade to 2022.1.6 (14.1.6)
- MOVEit Transfer 2022.0.x upgrade to 2022.0.5 (14.0.5)
- MOVEit Transfer 2021.1.x upgrade to 2021.1.5 (13.1.5)
- MOVEit Transfer 2021.0.x upgrade to 2021.0.7 (13.0.7)
- MOVEit Transfer 2020.1.x upgrade to 2020.1.6 (12.1.6)
- MOVEit Transfer 2020.0.x upgrade to one of the new versions listed above (or higher).
- MOVEit Cloud 14.0.5.x upgrade to 14.0.5.45
- MOVEit Cloud 14.1.6.x upgrade to 14.1.6.97
If possible, make sure your Progress Software’s MOVEit Transfer application is not exposed to the internet in order to refrain from exploitation. Given the amount of time the vulnerability is under active exploitation, it is advised to assume compromise and conduct a thorough incident response process while trying to identify any abnormal activity.
Conclusion
The persistent and widespread exploitation of the MOVEit CVE-2023-34362 vulnerability continues to pose significant risks to organizations. Despite the efforts to raise awareness and provide mitigation strategies, the number of compromised organizations continues to grow.
If you don’t want to be next on the list, make sure to upgrade your MOVEit version and refrain from exposing it over the internet.
About the author: Ofri Ouzan is a Security Researcher at Rezilion.