The Details of Microsoft’s September 2023 Patch Tuesday Release

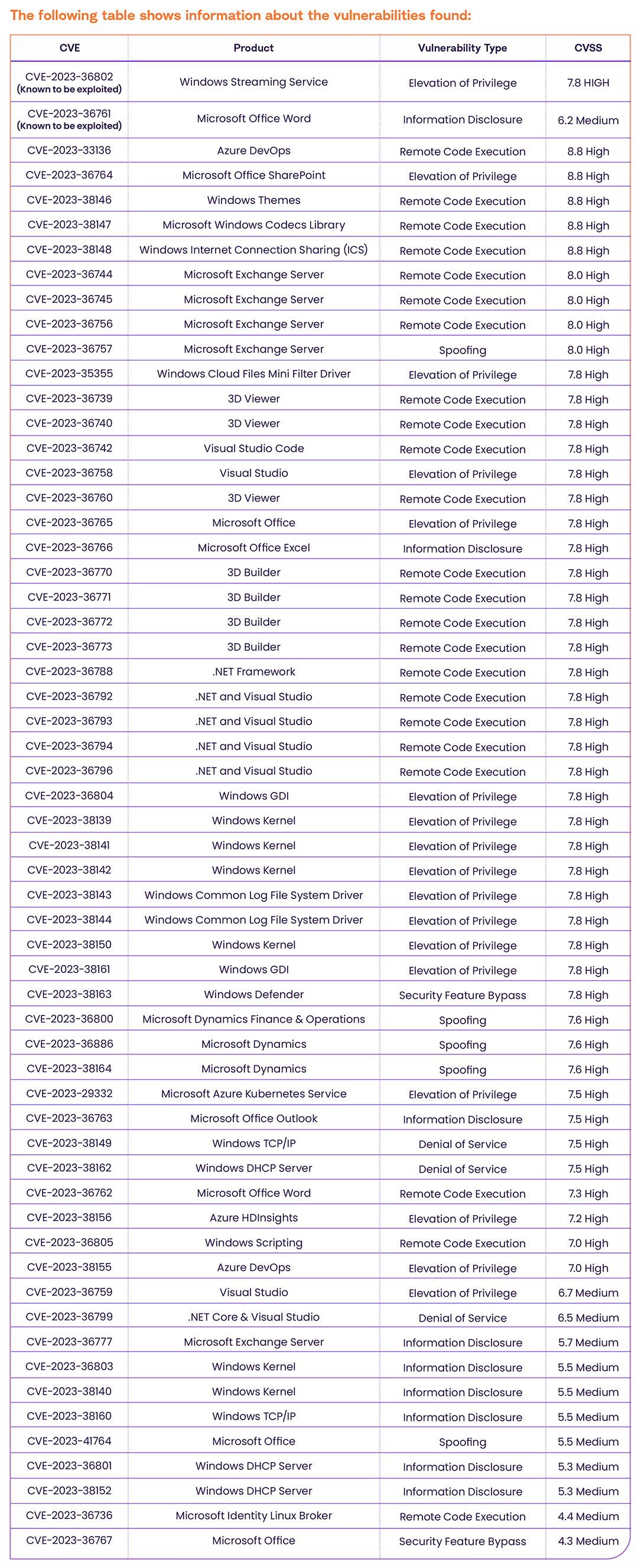
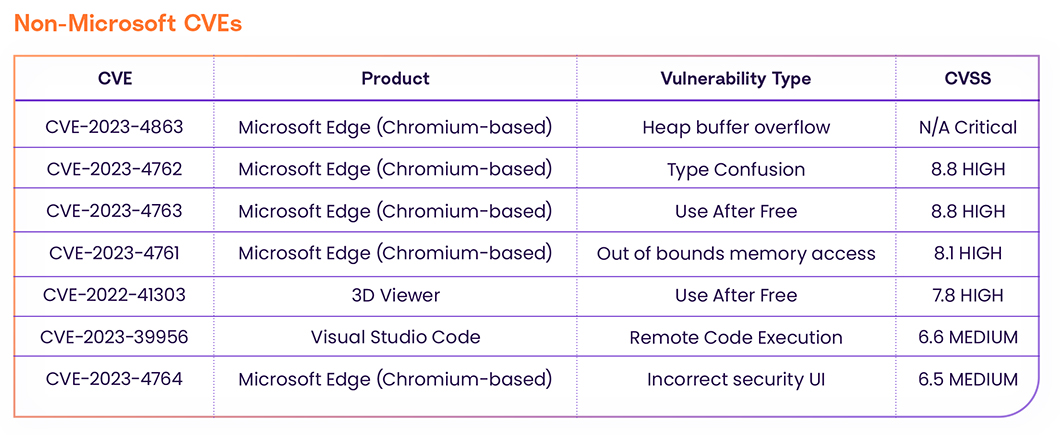
On September 12th, 2023, Microsoft released their September Patch Tuesday and revealed 59 Microsoft CVEs; 47 of them are HIGH severity and 12 of them are MEDIUM severity, along with 7 other non-Microsoft CVEs.
CVE-2023-36802 and CVE-2023-36761 are known to be exploited in the wild according to the CISA KEV Catalog. The vulnerabilities affect popular platforms such as 3D Viewer, Microsoft Office, .NET, Visual Studio, and more.
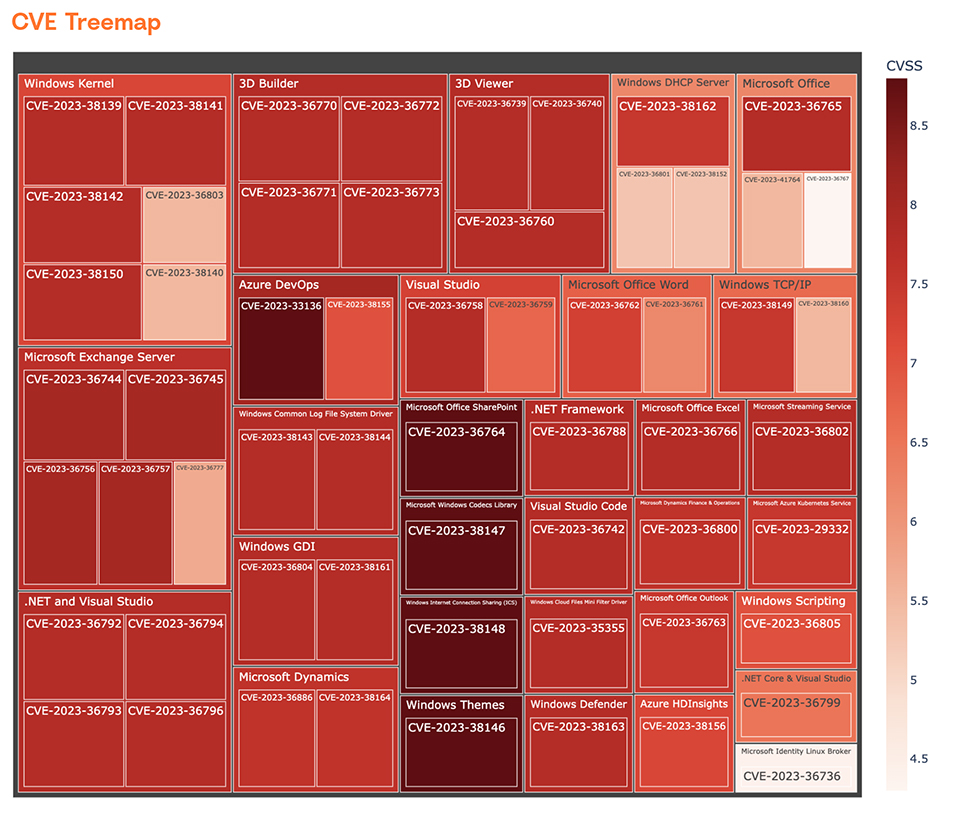
CVE Details For September 2023 Patch Tuesday
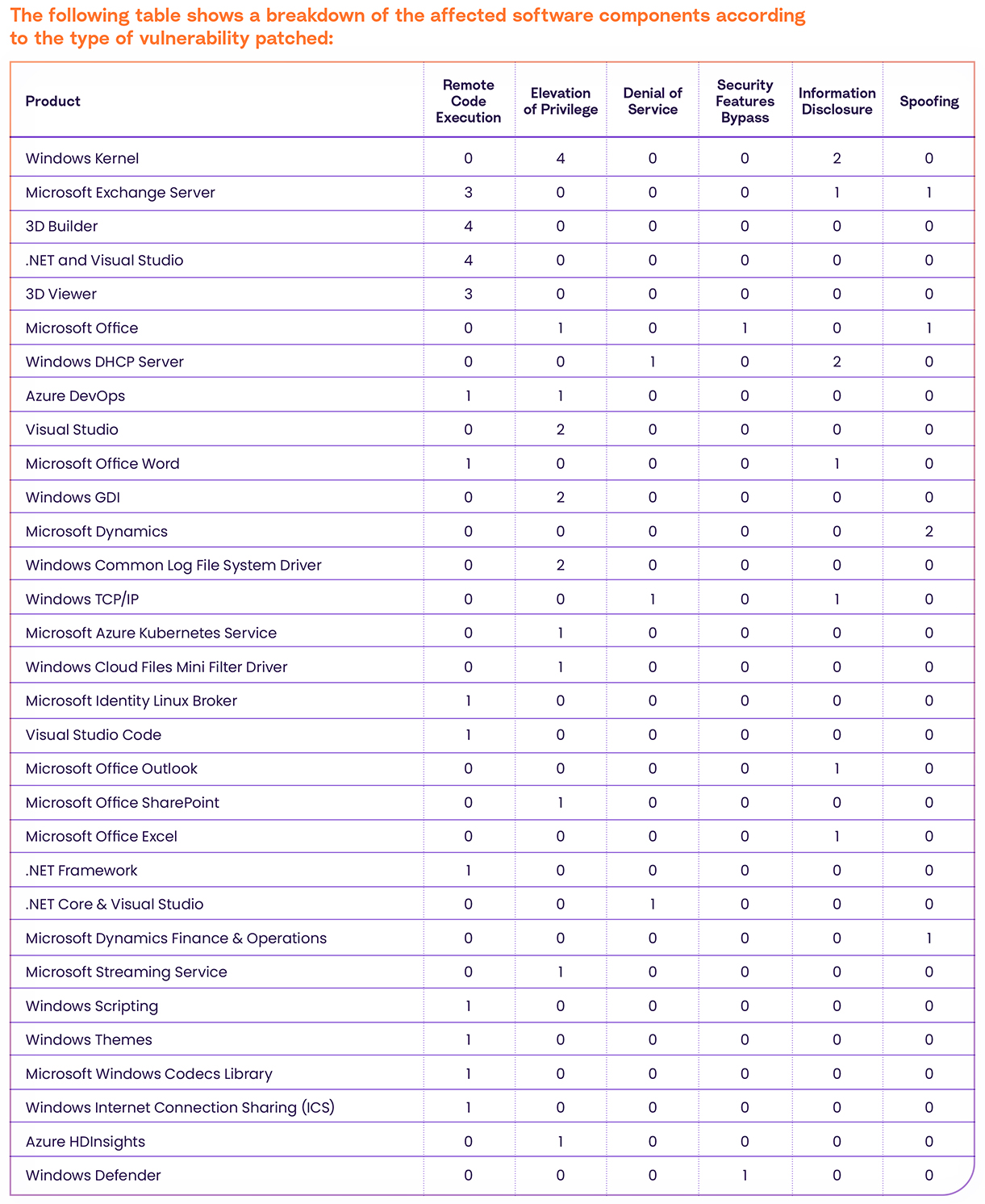
Affected Software Details
As you can see, the following products have the highest number of vulnerabilities:
- Windows Kernel (6) – The core component of the Windows operating system responsible for managing hardware resources and providing essential system services.
- Windows Exchange Server (5) – A robust email and calendaring server developed by Microsoft, commonly used in enterprise environments for email communication and collaboration.
- 3D Builder (4) – A user-friendly 3D modeling application for Windows, enabling users to create and edit 3D models for various purposes, including 3D printing.
- .NET and Visual Studio (4) – The .NET framework is a software development platform developed by Microsoft, while Visual Studio is an integrated development environment (IDE) used for creating software applications using the .NET framework.
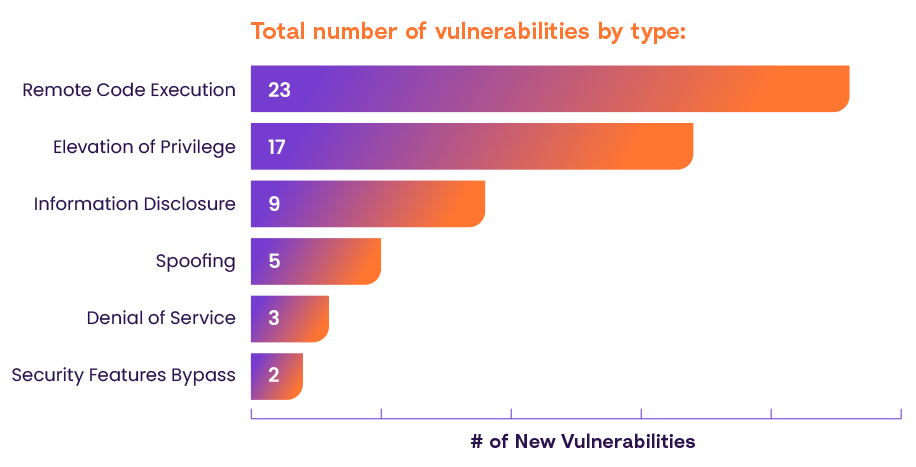
Vulnerability Types
The following vulnerabilities require extra attention:
CVE-2023-36802
CVE-2023-36802 is a 7.8 High severity Elevation of Privilege in Microsoft Streaming Service is known to be exploited in the wild, according to CISA and Microsoft Advisory.
An authenticated attacker can easily exploit the vulnerability locally and escalate privileges via the Microsoft Streaming Service. The vulnerability has an available exploit that works in most situations where the vulnerability exists.
CVE-2023-36761
CVE-2023-36761 is a 6.2 Medium severity Information Disclosure in Microsoft Office Word that is known to be exploited in the wild, according to CISA and Microsoft Advisory.
An unauthenticated attacker with low privileges can easily exploit the vulnerability locally and leak information via Microsoft Office Word. The vulnerability has an available exploit that works in most situations where the vulnerability exists.
Recommendations
If you have any of the affected products listed above in your environment, make sure to patch your system immediately. Additionally, prioritize patching of the known exploited vulnerabilities which now pose the highest risk among the September Patch Tuesday vulnerabilities.
About the author: Ofri Ouzan is a security researcher with Rezilion.