PWNKIT – What You Need to Know About It

By: Baksheesh Singh Ghuman and Ofri Ouzan
We are still recovering from the after effects of Log4j, but there is already a new vulnerability around the corner. PWNKIT, reported by Qualys’ research team, is a major Linux polkit (previously known as PolicyKit) related vulnerability. Like Log4j, which is the logging utility of Java, polkit is a systemd SUID-root program that controls system-wide privileges in unix-like operating systems. It is part of the default configuration and installation in every major modern Linux distribution, making it just as widespread and universal as Log4j.
The CVE associated with this vulnerability is CVE-2021-4034, however at this time no criticality has been assigned. RedHat has assigned it a criticality of 7.8, which puts it in the serious category.
What is PWNKIT
It is a serious memory corruption vulnerability that affects polkits pkexec. In addition to it being a serious vulnerability, it is also very easy to exploit. Pkexec is installed by default on all major Linux distributions. Using this vulnerability, a threat actor can gain full root privileges on any affected machine, computer, or asset. Once you have these elevated privileges, you can do significant damage.
A few things to note about this vulnerability is that its exploitability is not dependent on architecture or whether the polkit daemon is running or not. This makes it super easy to exploit. The good news is that it is a local exploit and is not remotely executable.
Who Can Use Pkexec
The threat is both internal and external. An internal threat actor using this vulnerability can gain root privileges. This is pretty straightforward. An external threat vector is where things get interesting. A threat actor can gain access to a machine via lateral access from another breach or attack and thus exploit this vulnerability. Even though it is a local exploit, it by no means poses a lesser risk.
Managing PWNKIT
Validate
If you have a Software Bill of Materials (SBOM), identify all occurrences of either policykit-1 or polkit. Each computer containing one of these packages should be patched (see the remediate section).
Any exploitation attempt will lead to the pkexec binary being loaded into memory. Monitoring or alerting on loaded instances of pkexec could signal potential exploitation attempts. When exploited, generally traces of exploits can be found in the logs. What makes PWNKIT dangerous is that it can be exploited without leaving a trace. So the first step is to discover the vulnerability and validate whether it is exploitable in your environment
Mitigations
Remove suid bit in pkexec file.
Remove execute permissions to everyone in pkexec file.
Change file user from root to another user.
Remediation
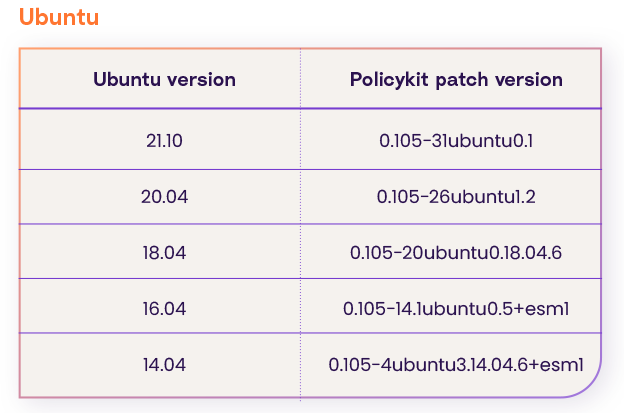
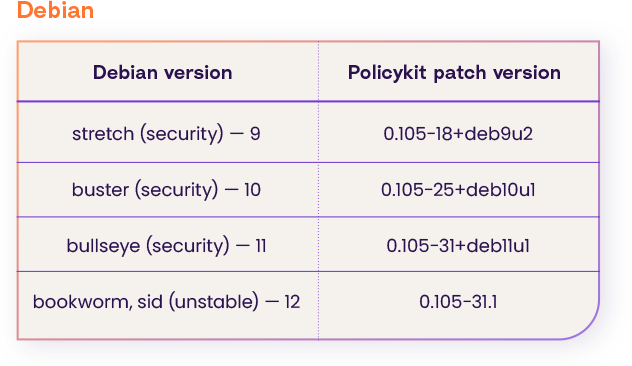
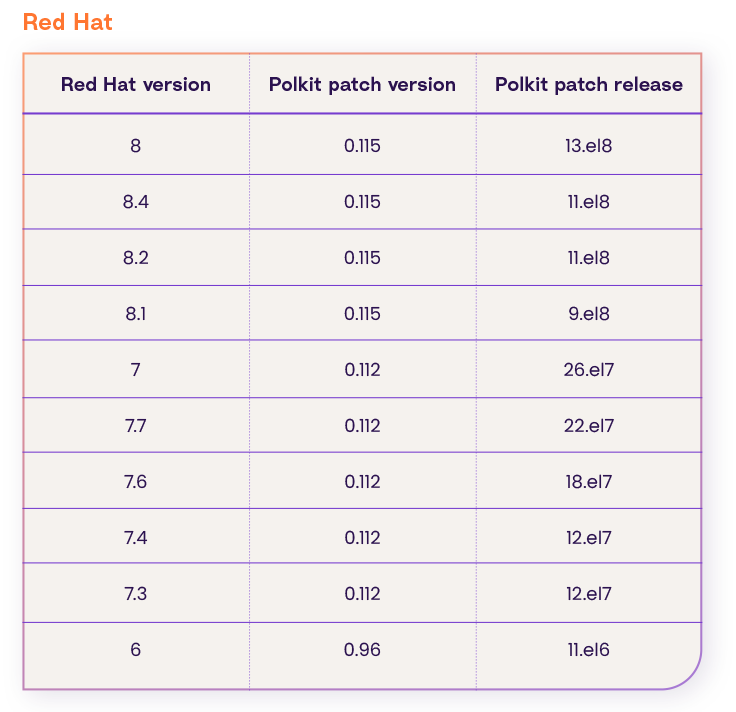
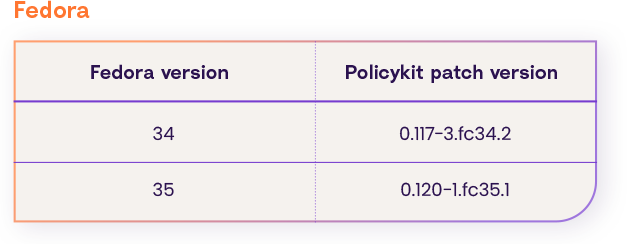
Upgrade the policy kit package version to one of these (according to your os distribution and version):
Suse
According to this page the policy kit package patch for all versions of suse is: 0.116-3.6.1
PWNKIT Timeline
Similarly to Log4j, this vulnerability has been living right under our noses and has gone undetected for over 12 years. Here is a timeline:
- May 2009 – Pkexec was created and has been vulnerable since then. It means that all subsequent versions of polKit were affected
- November 2021 – PwnKit was discovered by researchers from Qualys
- January 11, 2022 – Advisory and patch released
- January 25, 2022 – Coordinate disclosure by Qualys
How Can Rezilion Help
Given how easy it is to exploit this vulnerability, we expect public exploits will start and increase soon. Rezilion can help you stay ahead of this vulnerability and remain secure.
Using Rezilion’s dynamic SBOM you can get a comprehensive and continuous view of all your software components and quickly identify any PWNKIT related vulnerabilities and whether they are actually exploitable so that you can focus on your remediation efforts. Contact us today to get your free assessment.