Microsoft July 2023 Patch Tuesday Round Up

On July 11th 2023, Microsoft released their July Patch Tuesday and revealed 130 new CVEs, 5 of them are classified as “Exploitation Detected” by Microsoft and 4 of them added to the CISA KEV Catalog.
The vulnerabilities affect popular platforms such as Windows SmartScreen, Microsoft Office, Microsoft Office Outlook, Windows Error Reporting, Windows MSHTML Platform, and more.
According to NVD, 5 of the vulnerabilities are CRITICAL severity vulnerabilities, 75 are HIGH severity vulnerabilities and 50 have a MEDIUM severity CVSS score.
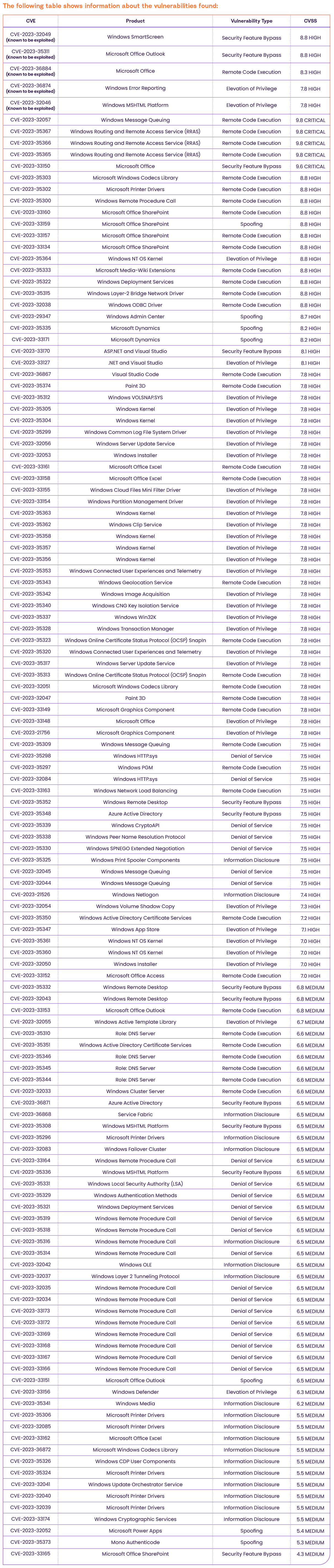
July’s Patch Tuesday CVE Details
Affected Software Details for July 2023 Patch Tuesday
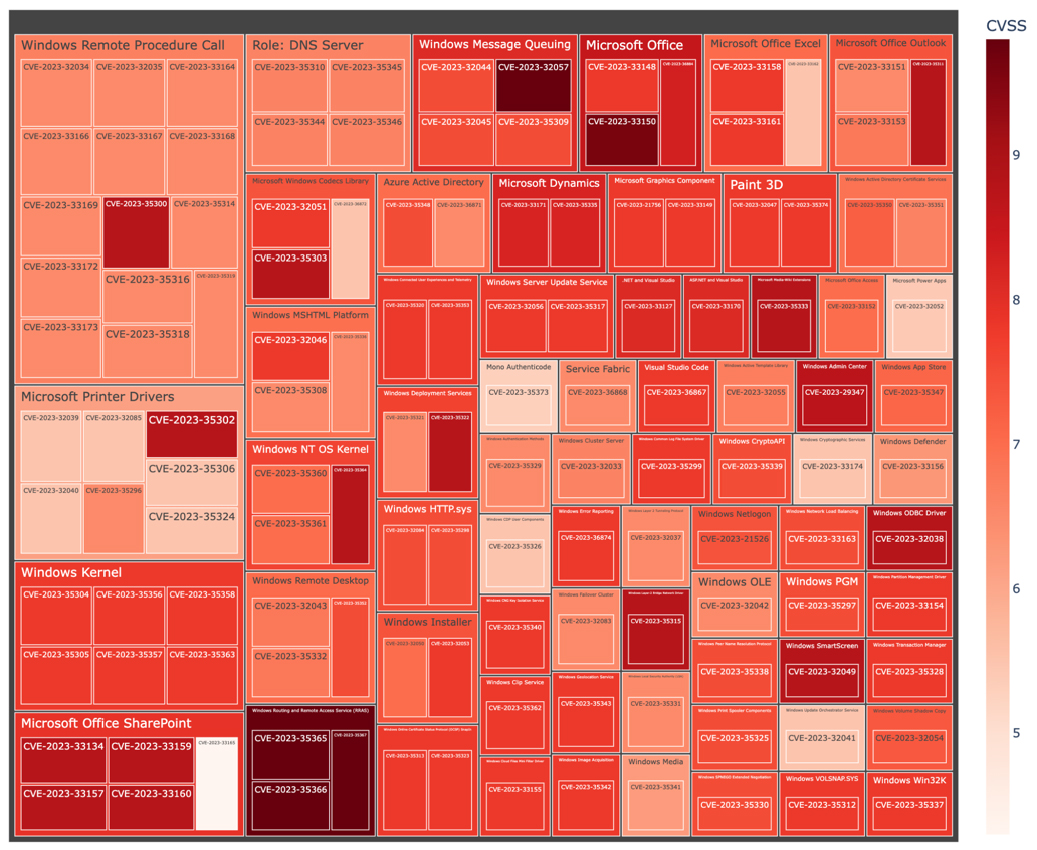
The following video diagram shows a breakdown of the affected software components according to the type of vulnerability patched:
As you can see, the following products have the highest number of vulnerabilities:
- Windows Remote Procedure Call (14) – is a communication protocol that allows programs to execute procedures remotely across a network, enabling interprocess communication between a client and server in the Windows operating system.
- Microsoft Printer Drivers (7) – are software components that allow Windows to communicate with printers, facilitating the translation of print commands and managing printer-specific features for various printer models and manufacturers.
- Windows Kernel (6) – is the core component of the Windows operating system that manages system resources, memory, and provides essential services for running processes, device drivers, and other system components.
- Microsoft Office SharePoint (5) – is a web-based collaboration and content management platform that integrates with Microsoft Office, enabling organizations to create intranet portals, document management systems, and team collaboration sites to facilitate information sharing, document collaboration, and workflow automation.
- Role: DNS Server (4) – resolves domain names to IP addresses, translating human-readable domain names into computer-friendly IP addresses for efficient network communication.
- Windows Message Queuing (4) – is a messaging infrastructure in Windows that allows applications to send and receive messages across various systems and networks, ensuring reliable and asynchronous communication between distributed components.
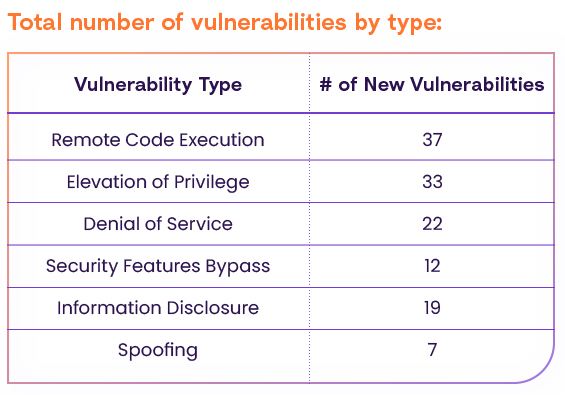
Vulnerability Types
The following vulnerabilities are known to be exploited and require extra attention:
CVE-2023-32049
CVE-2023-32049 CVE-2023-32049 is an 8.8 HIGH severity Feature Bypass vulnerability in Windows SmartScreen that is known to be exploited in the wild, according to CISA and Microsoft Advisory.
An unauthenticated attacker can easily exploit the vulnerability over the network and bypass a security feature in Windows SmartScreen. The vulnerability has an available exploit that works in most situations where the vulnerability exists.
CVE-2023-35311
CVE-2023-35311 is an 8.8 HIGH severity feature bypass vulnerability in Microsoft Office Outlook that is known to be exploited in the wild, according to CISA and Microsoft Advisory.
An unauthenticated attacker can easily exploit the vulnerability over the network and bypass a security feature in Microsoft Office Outlook. The vulnerability has an available exploit that works in most situations where the vulnerability exists.
CVE-2023-36884
CVE-2023-36884 is an 8.3 HIGH severity remote code execution zero day vulnerability in Microsoft Office that is known to be exploited in the wild, according to Microsoft Advisory.
An unauthenticated attacker can exploit the vulnerability and execute code through Microsoft Office. The vulnerability has an available exploit that works in most situations where the vulnerability exists, but a successful attack depends on conditions beyond the attacker’s control.
At the time of writing, Microsoft has not yet provided a patch for the vulnerability. For this reason, this vulnerability is not listed in the CISA KEV catalog; a patch is required to be included in the list.
Microsoft Threat Intelligence identified exploitation attempts by a Russian threat actor called Storm-0978 (AKA RomCom) against government agencies in Europe and North America. They conducted phishing campaigns using malicious Word documents, using lures related to the Ukrainian World Congress.
Mitigation
Since a patch is not available, affected users that do not use Microsoft Defender for Office 365 need to mitigate the vulnerability according to the following Microsoft Recommendations:
Activate the attack surface reduction rule named Block all Office applications from creating child processes, however, if not possible, set the following registry key: computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION
Add the following applications and set the Type field to REG_DWORD and the Data field to 1:
- Wordpad.exe
- WinWord.exe
- WinProj.exe
- Visio.exe
- PowerPoint.exe
- MsPub.exe
- MSAccess.exe
- Graph.exe
- Excel.exe
CVE-2023-36874
CVE-2023-36874 is a 7.8 HIGH Elevation of Privileges vulnerability in Windows error reporting that is known to be exploited in the wild, according to CISA and Microsoft Advisory.
An unauthenticated attacker can easily exploit the vulnerability locally and elevate privileges via Microsoft Office Outlook; an available exploit code of the vulnerability does not exist.
CVE-2023-32046
CVE-2023-32046 is a 7.8 HIGH severity Elevation of Privileges vulnerability in the Windows MSHTML platform that is known to be exploited in the wild, according to CISA and Microsoft Advisory.
An unauthenticated attacker can easily exploit the vulnerability locally and escalate privileges through the Windows MSHTML Platform; an available exploit code of the vulnerability does not exist.
Recommendations
If you have any of the affected products listed above in your environment, make sure to patch your system immediately. Additionally, prioritize mitigating CVE-2023-36884 and patching the known exploited vulnerabilities which now pose the most risk among the “July Patch Tuesday” vulnerabilities.
About the author: Ofri Ouzan is a security researcher with Rezilion.