April 2023 Patch Tuesday: 114 Vulnerability Fixes Released, Including One Actively Exploited in the Wild

On April 11th, 2023, Microsoft released their April Patch Tuesday roundup, which includes 114 new vulnerability fixes and 4 updates for existing CVEs. Of these fixes, 17 were published on April 6th and 97 were published on April 11th. One of the vulnerabilities has already been exploited in the wild.
The vulnerabilities impact several components, including Microsoft Edge, Microsoft Printer, Windows DNS, Windows Kernel, Visual Studio, Microsoft Office, and Windows Common Log File System. The National Vulnerability Database (NVD) has classified 2 of the vulnerabilities as CRITICAL, 76 as HIGH, and 40 as MEDIUM severity based on their CVSS scores.
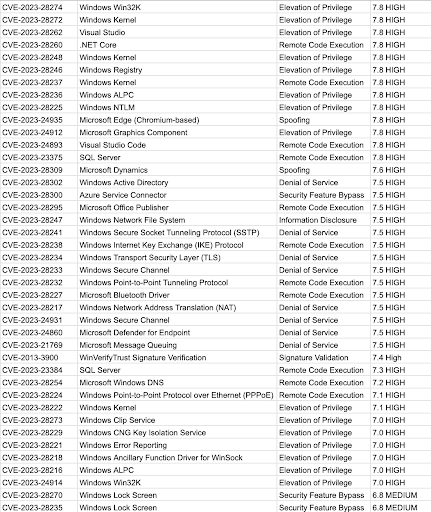
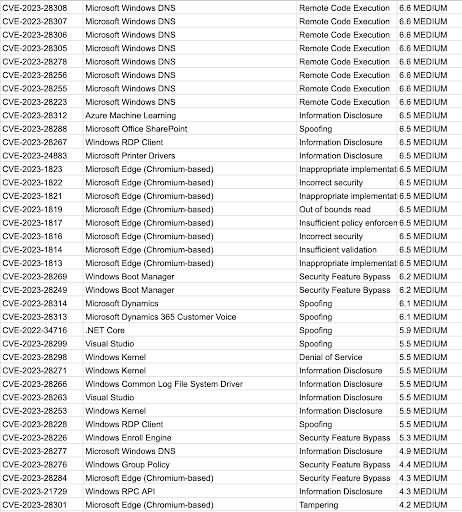
CVE Details For April 2023 Patch Tuesday
The following table shows information about the vulnerabilities found:
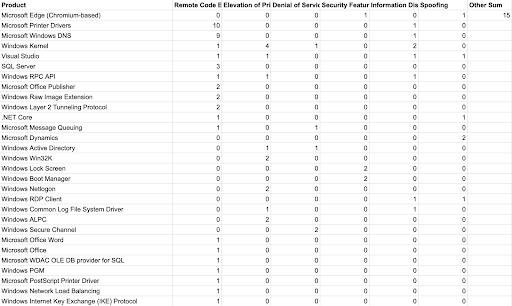
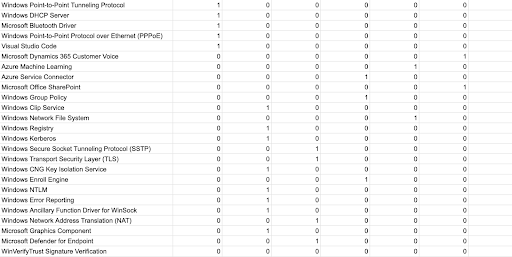
Affected Software Details
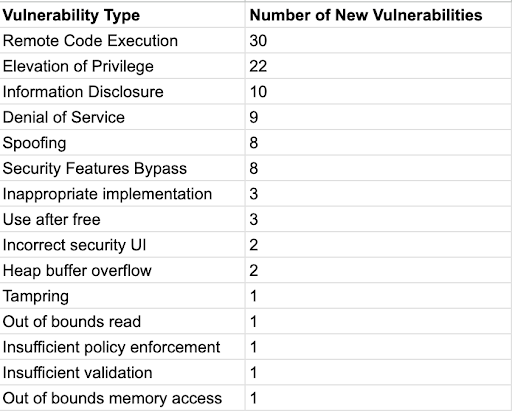
The following table shows a breakdown of the affected software components according to the type of vulnerability patched:
As you can see, the following products have the highest number of vulnerabilities:
Microsoft Edge (Chromium-based) (17) – Microsoft Edge is a web browser developed by Microsoft and is based on the Chromium open-source project.
Affected by the following vulnerabilities: Security Feature Bypass, Spoofing, Tampering, Inappropriate implementation, Incorrect security UI, Heap buffer overflow, Out of bounds read, Use after free, Insufficient policy enforcement, Insufficient validation, Out of bounds memory access, Signature Validation
Microsoft Printer Drivers (11) – Intelligent business applications that deliver alerts and notifications via Microsoft Teams or Outlook
Microsoft Windows DNS (10) – Domain name resolution services for local networks and the internet in Windows.
Windows Kernel (8)
Visual Studio (4) – An Integrated Development (IDE) for Microsoft.
Notable CVEs
CVE-2023-28252
CVE-2023-28252 is a 7.8 scored privilege escalation vulnerability found in the Windows Common Log File System (CLFS) driver in all supported versions of Windows that can elevate SYSTEM permissions, this vulnerability is a zero-day and is known to be exploited in the wild (according to CISA Known Exploited Vulnerabilities).
The Windows Common Log File System driver (clfs.sys) is a component of the Windows operating system that provides a general-purpose, transaction-based, object-oriented logging subsystem that is accessible to both kernel-mode as well as user-mode applications and system components. It is designed to provide a secure, reliable, and scalable logging infrastructure for use by developers.
The vulnerability was identified to be exploited in Nokoyawa ransomware by Genwei Jiang with Mandiant and Quan Jin with DBAPPSecurity WeBin Lab and reported it to Microsoft.
This is the second CLFS elevation of privilege zero-day exploited in the wild this year, and the fourth in the last two years. It is also the second CLFS zero-day disclosed to Microsoft by researchers from Mandiant and DBAPPSecurity
CVE-2023-28250
CVE-2023-28250 is a 9.8 Critical Remote Code Execution vulnerability in the Pragmatic General Multicast protocol installed with the MSMQ service, which could allow an attacker who successfully exploited this vulnerability to send a specially crafted file over the network to achieve remote code execution and attempt to trigger malicious code.
CVE-2023-21554
CVE-2023-21554 is a 9.8 Critical Remote Code Execution vulnerability in the Microsoft Message Queuing service that can be triggered with a specially crafted malicious MSMQ packet sent to an MSMQ server from an unauthorized user via 1801/TCP.
It is important to note that when installing Microsoft Exchange Server, the setup wizard app would enable the MSMQ service in the background if the user selects the “Automatically install Windows Server roles and features that are required to install Exchange” option, which is recommended by Microsoft.
Recommendations
We highly recommend patching any security issues discovered by Microsoft on your Microsoft devices, with special attention given to the zero-day vulnerability that is currently being actively exploited and poses the highest risk. Additionally, for users of Microsoft Exchange, it is critical to check your systems for the identified critical vulnerabilities and patch them immediately. To ensure maximum protection, we recommend using a firewall to scan for open 1801 ports and closing them if found. For those planning to install Microsoft Exchange, we advise against enabling the installation of the Windows Server roles and features, unless absolutely necessary. By following these recommendations, you can help protect your systems and data from potential attacks.