Shore Up Defenses Now to Guard Against Attacks Amid Russia-Ukraine Conflict

By: Yotam Perkal, Head of Vulnerability Research, Rezilion
A Timeline of Russian-Led Cyberattacks
The recent invasion of Russian troops into Ukraine territory was preceded by a blitz of cyberattacks targeting banking systems, government websites, and critical infrastructure.
The cyberattacks started long before Russian troops began to descend on Ukraine borders. Cyberattacks date back to 2015 when the Russian intelligence organization, the GRU, targeted Ukraine’s industrial control systems networks with malware. This left approximately 230,000 homes in the Ivano-Frankivsk region without power for roughly six hours.
In 2017, Ukraine was hit by the destructive NotPetya ransomware in what is considered one of the most destructive cyberattacks in history. The NotPetya malware attached itself to MeDoc, Ukraine’s most popular tax-filing software, via a supply-chain attack which compromised the software’s automatic update system. This enabled the ransomware to effectively spread across Ukraine affecting about 400,000 customers, and eventually also contaminated machines worldwide. Upon infection, the malware encrypted all of the files on the infected hosts and demanded users to pay a ransom in Bitcoin in order to receive instructions to decrypt the files. In most cases, complete restoration wasn’t possible. The NotPetya campaign is considered one of the most costly cyberattacks to date, with estimated damages of around $10 billion.
Over nine months in 2021, more than 1,200 cyberattacks or incidents were neutralized, according to Ukraine’s SBU security service.
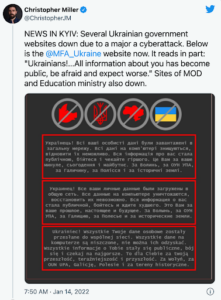
On January 14th, a massive attack brought down approximately 70 Ukrainian government websites, accompanied with an ominent “prepare for the worst” message.
On February 15th, numerous powerful Distributed Denial of Service (DDoS) attacks, caused disruption of services of several state-owned banks, namely Privatbank and Oschadbank, as well as some government agencies. That day, Privatbank customers received fake SMS messages, allegedly from the Ukranian cyber police, claiming that the bank ATMs were down. The messages were later deemed fake and were apparently just part of an “information attack.”
Most recently, a day before Russia began to mobilize ground forces into Ukraine, an additional cyberattack commenced. This time, a combination of a DDoS attack, followed by a sophisticated data wiping malware dubbed HermeticWiper, which affected hundreds of machines across Ukraine.
The Supply Chain Risk
There are a few characteristics worth highlighting regarding the HermeticWiper malware as they are representative of many APT (Advanced Persistent Threat) or state sponsored malware campaigns:
Early Access to the System
The Symantec research team highlighted that in at least one occasion, attackers established control in the victims’ network two months before the actual attack:
“In the case of an attack against one organization in Ukraine, the attackers appear to have gained access to the network on December 23, 2021, via malicious SMB activity against a Microsoft Exchange Server. This was immediately followed by credential theft. A web shell was also installed on January 16, before the wiper was deployed on February 23.”
This method isn’t new. In the SolarWinds attack, Russian-backed actors presumably compromised the supply chain of the widely used SolarWinds’ Orion® IT monitoring software by injecting a malicious update. The attackers remained undetected for approximately 9 months.
The attack was discovered one year after the attackers first gained access to Solarwinds’ build system, and evidently affected more than 100 American companies and various government agencies.
Exploitation of Known, Unpatched Vulnerabilities
Historically, nation-state sponsored APT groups exploit known vulnerabilities as part of their attack chain. In the HermeticWiper case for example, initial access was shown to rely on known vulnerabilities in the Microsoft Exchange Server.
In another case, attackers appear to have exploited a known vulnerability in the Microsoft SQL Server (CVE-2021-1636).
Common vulnerabilities known to be exploited by Russian state-sponsored APT actors for initial access include (source: CISA):
• CVE-2018-13379 FortiGate VPNs
• CVE-2019-1653 Cisco router
• CVE-2019-2725 Oracle WebLogic Server
• CVE-2019-7609 Kibana
• CVE-2019-9670 Zimbra software
• CVE-2019-10149 Exim Simple Mail Transfer Protocol
• CVE-2019-11510 Pulse Secure
• CVE-2019-19781 Citrix
• CVE-2020-0688 Microsoft Exchange
• CVE-2020-4006 VMWare (note: this was a zero-day at time)
• CVE-2020-5902 F5 Big-IP
• CVE-2020-14882 Oracle WebLogic
• CVE-2021-26855 Microsoft Exchange (Note: this vulnerability is frequently observed used in conjunction with CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065)
You can probably add CVE-2021-44228 (Log4Shell) to that list as it was identified as being leveraged by several Iraninan and Chinese APT groups.
Utilizing Existing Tools in the Environment, Also Known As “Living of the Land”
Another common practice seen by these APTs, which was also evident in HermeticWiper, is the use of common tools existing in the compromised environment.
Tools such as `powershell`, `cmd.exe`, and scheduled tasks, which are in use as part of most system’s normal operations, can avoid detection of most EDR systems.
This is a good point to highlight that any environment that does not require use of such tools, must be explicitly disabled.
Shields Up: Best Practices for Defense Against Retaliatory Attacks
While there are currently no concrete threats to organizations outside of the conflict area, it is likely that at some point Russian threat actors will direct their efforts against NATO and EU member states as a retaliation for supporting Ukraine and imposing sanctions.
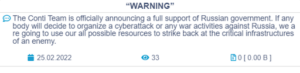
The Conti ransomware group, a claimed state-sponsored threat actor, has already threatened in retaliation in the event cyberattacks are conducted against Russia. In a message posted on the groups’ official website, the group states that they would target any “enemy” critical infrastructure.
The message was later modified to a “softer” version excluding the specific threat against critical infrastructure.
CISA has issued a ‘Shields Up’ warning calling for a heightened readiness for potential attacks:
“We are mindful of the potential for Russia’s destabilizing actions to impact organizations both within and beyond the region, particularly in the wake of sanctions imposed by the United States and our Allies. Every organization, large and small, must be prepared to respond to disruptive cyber activity”
In light of this warning, here are some recommendations that will be beneficial for organizations to adopt.
Shorten Patching SLAs
As was shown in the past by the CISA patching directive, one of the most effective ways to reduce exploitation risk is to reduce your attack surface by patching existing vulnerabilities.
Shorten your SLAs for addressing vulnerabilities while specifically targeting known exploited vulnerabilities.
Visibility is Key
Make sure you have an up-to-date Software Bill of Materials (SBOM). This will allow you to quickly identify vulnerable elements in your environment and will save you valuable time.
Know your environment and keep your eyes open for any divergence from the norm. This of course assumes you know what normal is. For that purpose, use white lists. Are there new running processes you haven’t seen before? Is there any abnormal outbound traffic?
Human Analysis is Essential
Don’t blindly rely on automatic tools as they all have blindspots and, with enough willingness, can be circumvented. A recent study Rezilion researchers conducted after Log4j was first revealed is a good example of the divergence in logic and detection capabilities between different tools that supposedly do the same thing.
The research showed that most scanners used to detect vulnerable Log4Shell components have detection gaps:
Machine learning based tools have also proven to be susceptible to circumvention. Historically, most such state sponsored attacks rely on tools that are already present in the victims environment (referred to as Living off the Land) which makes detection by EDR tools challenging.
In cases in which small changes are made in order to avoid signature based detection, there is no replacement for a pair of human eyes. In most such cases that will fool a signature/rule will still be identified by a skilled analyst.
Enable Logging with Sufficient Granularity
Robust logging is critical for allowing effective identification and triage of unusual activity across your stack.
Test Your Security Controls
Make sure you have playbooks in place and that your team is practiced in applying them.
Test Backups
Lastly, regularly test backup procedures and ensure that backups are isolated from network connections. This is especially important in light of the HermeticWiper malware recently used against Ukrainian targets. CISA has also issued a very detailed alert containing guidelines for detection, mitigation, and recovery from such events.
Cyber Defense Beyond Today’s Headlines
It is important to note, these recommendations are by no means only relevant in regards to recent events. Effective cyber defense is an ongoing effort that requires sustained strategic investment. An organization that lacks basic security hygiene such as multi-factor authentication, strong password policies, a vulnerability management program, and an overall security awareness mindset isn’t something that can be instantly “fixed” by applying recommendations given in a blog post.
Moreover, there isn’t a button you could push and immediately be immune to these types of attacks. It is debatable if there are any steps you can take in order to fully protect your environment from such a nation state threat.
That said, this doesn’t mean you shouldn’t try. You shouldn’t however focus on prevention, but instead make sure you are able to detect and respond. Assume compromise at the base level and plan from there.