Rezilion Releases MI-X, A New Open Source Vulnerability Validation Tool

By Ofri Ouzan and Yotam Perkal, Rezilion Research
We are excited and proud to announce the release of Am I Exploitable? (MI-X), a tool that allows researchers and developers to know if their containers and hosts are impacted by specific, high-profile vulnerabilities.
MI-X, developed by Rezilion’s vulnerability research team, made its debut this week at Black Hat Arsenal, and is now officially available as an open-source project.
The introduction of MI-X is the first of a series of initiatives planned by Rezilion to foster a community around detecting, prioritizing, and remediating software vulnerabilities.
What problem does MI-X solve?
Rezilion’s research team closely monitors every new critical vulnerability discovered. We noticed that the first question people ask themselves whenever such a high-profile vulnerability is announced is: “Do I have the vulnerable component present in my environment, and if so, where?” The question that immediately follows is: “Am I impacted by it?”
While there are mature tools that can answer the first question, such as standard vulnerability scanners or various software composition analysis tools, we realized that there is a gap when it comes to tools that can effectively answer the second question of whether or not an organization is impacted by a vulnerability.
That is the gap MI-X tries to address.
Each time a new high-profile vulnerability surfaces, we see an abundance of ad-hoc tools released with the objective of helping to answer the “Am I affected?” question. The problem is, that these tools are often written in a haste, by different vendors/security researchers, each with its own implementation approach, and are not always actively maintained once public interest in the vulnerability subsidies. As we have seen with Log4Shell, these tools often have detection gaps and blindspots.
Current Vulnerability Tools Don’t Factor In Exploitability
Another critical component MI-X addresses is the actual exploitability of vulnerabilities. It is important to understand that a vulnerable package installed on your environment does not necessarily mean that the vulnerability is exploitable.
There are multiple factors that affect exploitability and these factors may vary for each vulnerability. These factors include:
- Is the operating system in question susceptible to the vulnerability?
- Is the vulnerable component loaded to memory?
- Is the required configuration in place?
- Is there a patch installed?
- Are there any compensating controls that mitigate the risk?
And more…
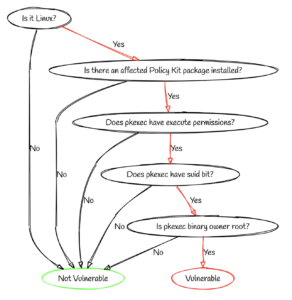
While standard vulnerability scanners simply do not take these factors into account, MI-X considers all them when reaching a decision and can also provide a graphical representation of the logical flow it took when reaching a decision. For example, see the decision tree for determining exploitability for the PwnKit vulnerability (CVE-2021-4034).
MI-X lets you identify and establish the exploitability of 20+ high-profile CVEs, with additional CVEs planned to be added on a regular basis.
Supported vulnerabilities include: Log4Shell, Spring4Shell, PwnKit, ShellShock, Dirty Cow, Dirty Pipe, Nimbuspwn and more.
Our vision for MI-X is that it will be a key asset for security teams that seek to know if critical vulnerabilities pose an actual threat to their individual software environment so they can properly assess the risk and plan a course of action.
In time, we hope to build a community of security researchers who will contribute their knowledge and expertise toward a single tool that will help individuals or organizations to quickly assess whether they are actually vulnerable to a specific vulnerability and why.
Want to try it out? A demonstration video similar to the one presented at BlackHat USA 2022 is available here. You can also read the (what do we call the one page?)to learn more about how to use MI-X. If you have any feedback or would like to report any bugs, please feel free to do so via discussions and issues. We look forward to your feedback & contributions.
For more information on getting started with MI-X, visit https://www.rezilion.com/rezilion-tools/am-i-exploitable/or join the tool’s open Slack channel at https://www.rezilion.com/lp/join-the-mi-x-community-on-slack/ .
If you find the tool useful, we’d love a star on the Rezilion/mi-x GitHub repository,