Patch Tuesday May 2023: Microsoft Addresses 49 Vulnerabilities

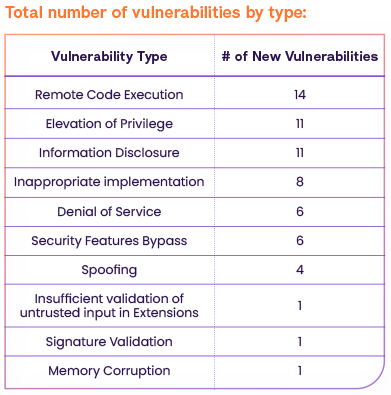
On May 9th 2023, Microsoft released their May Patch Tuesday and revealed 38 vulnerabilities fixes, 11 vulnerabilities fixes published on May 5th (9 of them are in the Microsoft Edge (Chromium-based, non-Microsoft CVEs) ) and 14 updates to old CVEs.
The vulnerabilities affect popular platforms such as Microsoft Edge , Microsoft Office Excel, Microsoft Bluetooth Driver, Microsoft SharePoint, and more.
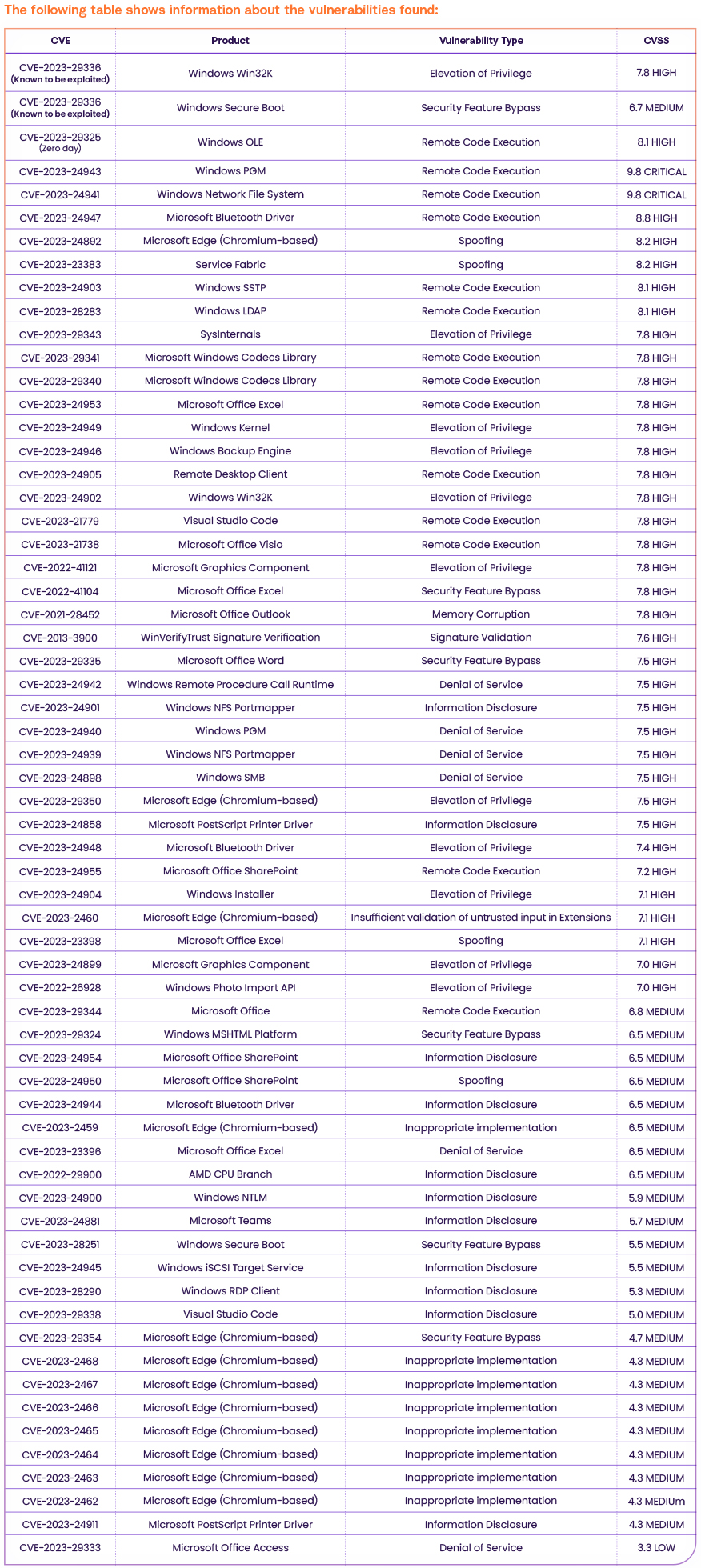
According to NVD, 2 of the vulnerabilities are CRITICAL severity vulnerabilities, 35 are HIGH severity vulnerabilities, 27 have a MEDIUM severity CVSS score and one is ranked as LOW severity and one still did not get a CVSS score.
CVE Details For Microsoft Patch Tuesday, May 2023
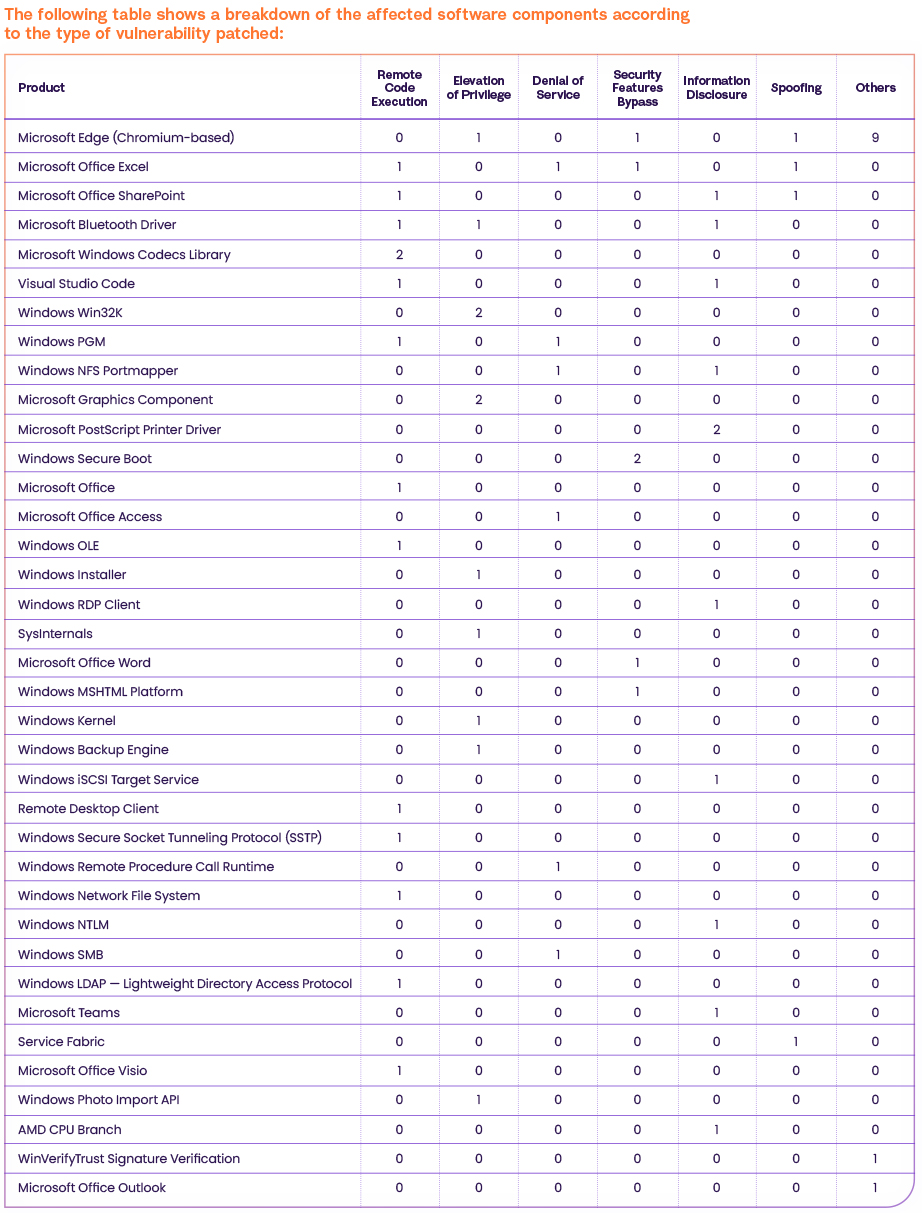
Affected Software Details
As you can see, the following products have the highest number of vulnerabilities:
-
- Microsoft Edge (Chromium-based) (12) – Microsoft Edge is a web browser developed by Microsoft and is based on the Chromium open source project.
Affected by the following vulnerabilities: Security Feature Bypass, Spoofing, Tampring, Inappropriate implementation, Incorrect security UI, Heap buffer overflow, Out of bounds read, Use after free, Insufficient policy enforcement, Insufficient validation, Out of bounds memory access, Signature Validation - Microsoft Office Excel (4) – a spreadsheet application developed by Microsoft for Windows for various tasks involving data management, analysis, and visualization.
- Microsoft Office SharePoint (3) – a web-based collaboration and content management platform that allows organizations to manage and share information and documents across teams and departments.
- Microsoft Bluetooth Driver (3) – a software component that enables Bluetooth functionality on Windows-based devices.
- Microsoft Edge (Chromium-based) (12) – Microsoft Edge is a web browser developed by Microsoft and is based on the Chromium open source project.
Vulnerability Types
The following vulnerabilities require extra attention:
CVE-2023-29336 – Privilege Escalation in Microsoft Win32k
CVE-2023-29336 is a 7.8 Critical Privilege Escalation vulnerability in the Microsoft Win32k which is known to be exploited according to the CISA KEV catalog. Win32k is a key component of the Windows operating system that provides the kernel-level support for the graphical user interface (GUI). Attackers successfully exploiting the vulnerability gain SYSTEM privileges.
CVE-2023-24932 – Security Feature Bypass in Secure Boot
CVE-2023-24932 is a 6.7 Medium Security Feature Bypass vulnerability in the Secure Boot feature. Secure Boot is a security feature implemented in modern computer systems that ensures that only trusted software is allowed to execute during the boot process. It uses digital signatures to verify the authenticity of each piece of software, including the operating system kernel, boot loader, and other critical system components, before they are loaded into memory and executed. If an attacker is able to bypass secure boot, they can load malicious software that is not signed and trusted by the system firmware and operating system. This can lead to persistent and stealthy attacks that are difficult to detect and remove, as the malicious software will be loaded before the operating system and security software.
This vulnerability is known to be exploited by threat actors to install the BlackLotus UEFI bootkit. UEFI bootkits are malware that is planted in the system firmware, making them invisible to security software running within the operating system. BlackLotus has been detected in-the-wild by the end of 2022, it has been sold on hacker forums since October 2022 and has evolved over time, with the developers improving the malware to bypass Secure Boot even on fully patched Windows 11 systems.
CVE-2023-29325 – Remote Code Execution in Windows OLE
CVE-2023-29325 is a 8.1 High Remote Code Execution vulnerability in Windows OLE. OLE stands for Object Linking and Embedding and is a technology developed by Microsoft for integrating different software components within a single document or file. OLE allows users to create compound documents that contain embedded objects from other applications.
The vulnerability can take advantage of emails that have been specially crafted. The flaw allows an attacker to execute remote code on the victim’s device by either a victim opening a specially crafted email with an affected version of Microsoft Outlook software or Outlook showing a preview of a specially crafted email. A “race” condition must be won by the attacker, who must also take additional steps to successfully exploit the vulnerability.
Recommendations
If you have any of the affected products listed above in your environment, make sure to patch your system immediately. Additionally, prioritize patching of the known exploited vulnerabilities which now pose the highest risk among the May 2023 Patch Tuesday vulnerabilities.