New Critical Flaw in OpenSSL: How to Know if You’re at Risk
According to their recent announcement, the Open SSL project will release a new version of OpenSSL (version 3.0.7) on Tuesday, November 1, which will include a patch for a new, critical CVE. Here at Rezilion, we are closely monitoring this issue, and as we await more information in the coming days, we’d like to take this moment to raise awareness among our customers and follower community, as this is likely to be a wide-spread issue and there are important actions that can be taken now to prepare.
About the OpenSSL Critical Flaw
As reported in Dark Reading, on October 26th, the OpenSSL Project announced a “critical” vulnerability in versions 3.0 and above of the vastly-popular cryptographic library for encrypting communications on the Internet.
While details and characteristics of the flaw have not yet been released, the critical classification of the vulnerability is notable as it’s only the second time the OpenSSL Project has addressed a flaw classified as “critical” (the first and only other time they’ve done so was for 2014’s Heartbleed Bug.). The timing of their notification, which was transparently shared to their mailing list and on Twitter on October 25th, is also notable, as it came five days before the patch was to be released — a longer-than-average advance warning window to give teams valuable time to prepare.
According to the team’s security policy, a vulnerability of critical severity “affects common configurations and which are also likely to be exploitable. Examples include significant disclosure of the contents of server memory (potentially revealing user details), vulnerabilities which can be easily exploited remotely to compromise server private keys or where remote code execution is considered likely in common situations.”
Potential Impact
OpenSSL is an open source version of the SSL and TLS security protocols, which provide encryption and server authentication over the Internet. Any significant security flaw in OpenSSL technology has the potential for massive impact, due to the ubiquitous usage of the software library by a wide variety applications, which include operating systems (Linux, Windows and MacOS), email servers, and the majority of internet servers powering HTTPS websites.
As the world awaits a more thorough disclosure next week, trade publications and industry experts alike are already drawing parallels between this week’s flaw and the Heartbleed Bug (CVE-2014-0160) of 2014. In this previous critical incident, anyone on the internet could read the memory of the systems — including servers, routers and other vulnerable devices — protected by vulnerable instances of the OpenSSL software. This had sweeping ramifications, as it allowed attackers to effectively “eavesdrop” on communications, steal PII (Personally Identifiable Information) data like names, passwords and other content, and impersonate services and users.
In 2014, organizations notoriously took months to detect and patch all of their vulnerable instances of the bug, which ultimately put millions of consumers, corporations and governments at risk when their data was captured in Heartbleed exploits.
How to Prepare
If there’s anything we learned from Heartbleed, it’s that time is of the essence when it comes to addressing the risk of critical CVEs.
Until a patch is made available on Tuesday, November 1, we strongly recommend checking your environment now to identify the presence of any instances of OpenSSL version 3.X. If you are using the Rezilion platform, you can also determine whether or not detected instances are actually exploitable within your environment by leveraging the platform’s Validation features to monitor their runtime execution.
Already a customer?
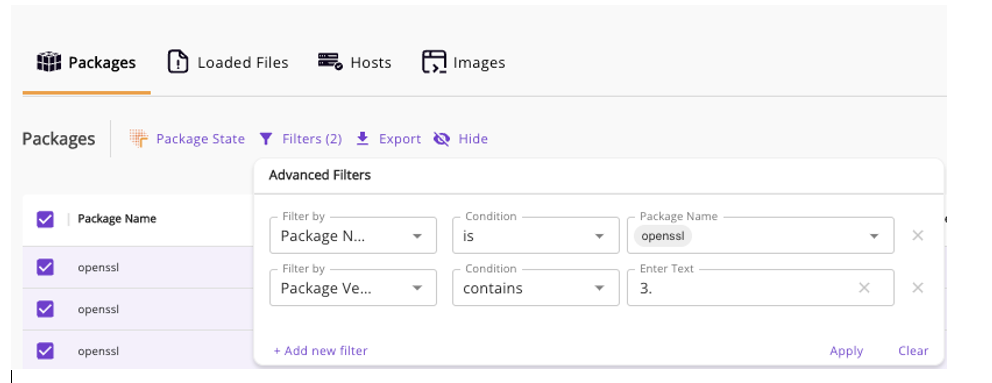
Check you environment by going to https://app.rezilion.com/inventory/packages and entering a filter such as the following:
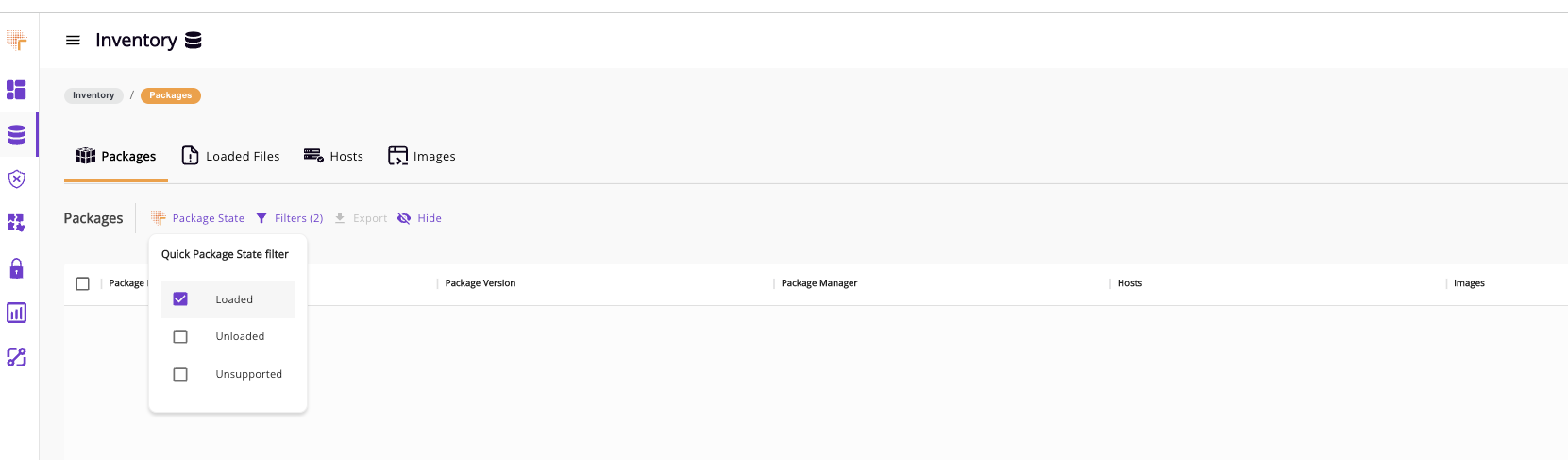
To further determine your risk, you can also use Rezilion’s “Package State” feature to see if detected vulnerabilities are exploitable in the context in which they appear in your environment.
New to Rezilion?
Receive a free OpenSSL assessment today at https://www.rezilion.com/lp/openssl-flaw-know-if-youre-at-risk-and-take-action/ to know your risk and develop an action plan.
***Updated 11/01/2022
OpenSSL Project has released their official security advisory with two different vulnerabilities, neither of which is critical: CVE-2022-3602 and CVE-2022-3786. Rezilion’s research team has a full analysis of the two vulnerabilities and recommendations for remediation in this updated blog post.