Microsoft February Patch Tuesday Addresses 78 Vulnerabilities, Including 3 Known Exploits

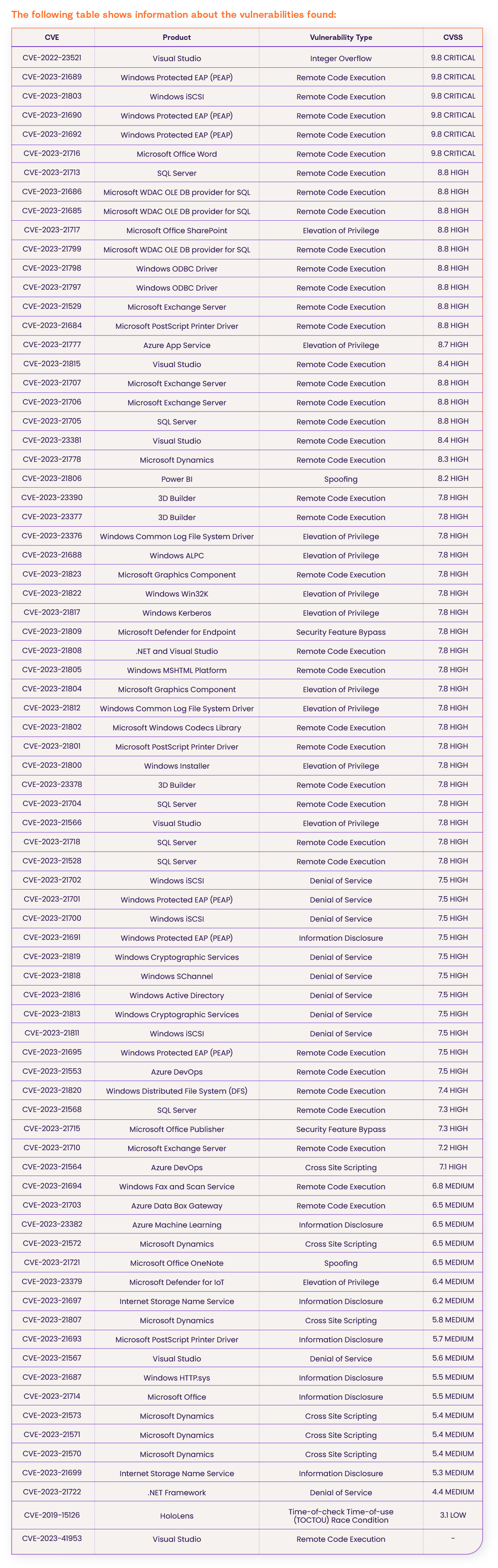
On February 14th 2023, Microsoft released their February Patch Tuesday and revealed 78 vulnerabilities fixes, including three known exploited vulnerabilities in the wild.
The vulnerabilities affect popular platforms such as Visual Studio, 3D Builder, SQL Servers, .NET Framework, Microsoft SharePoint, Microsoft Office, Exchange servers, and more.
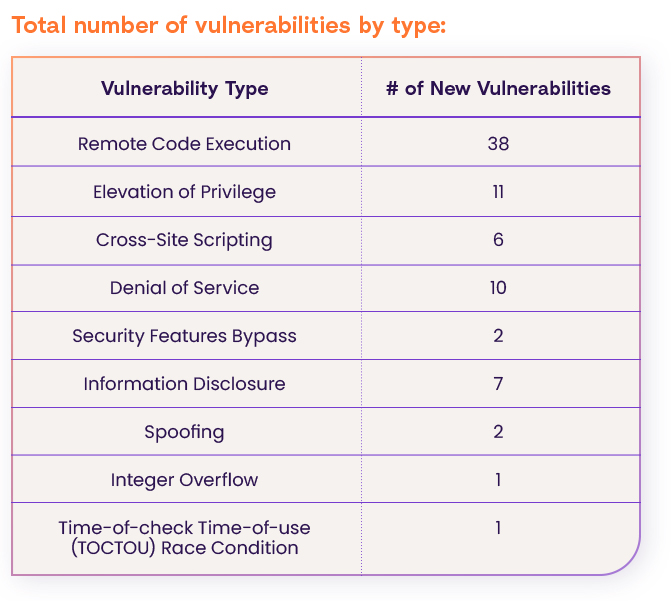
According to NVD, 6 are CRITICAL severity vulnerabilities, 53 are HIGH severity vulnerabilities, 17 have a MEDIUM severity CVSS score, one is ranked as LOW severity and one still did not get a CVSS score.
CVE Details for February 2023 Patch Tuesday
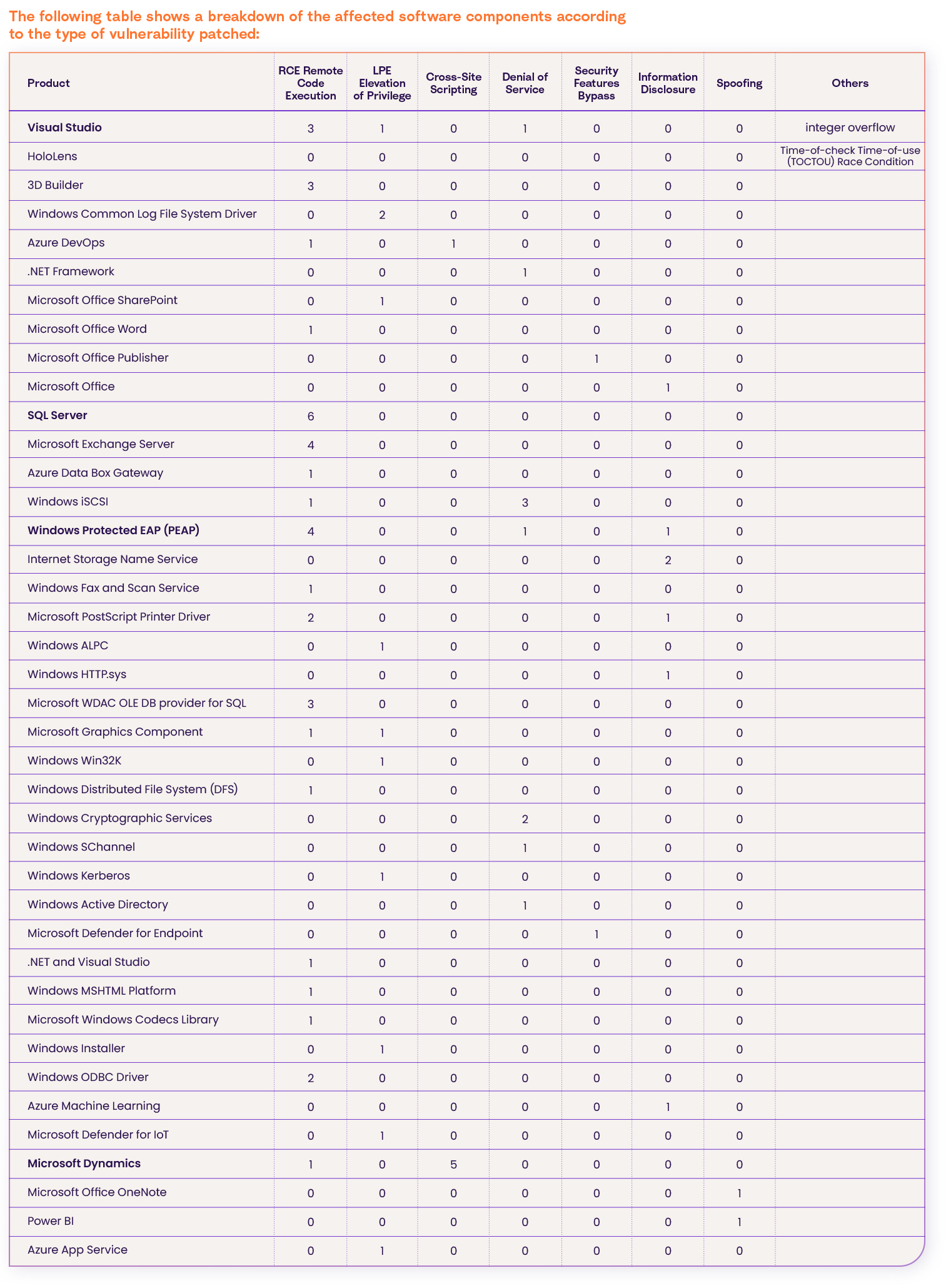
Affected Software Details
As you can see, the following applications have the highest number of vulnerabilities:
-
- Visual Studio – an Integrated Development (IDE) for Microsoft.
- SQL Server – Microsoft relational database management system
- Windows Protected EAP (PEAP) – a windows protocol that provides extensibility for authentication methods for commonly used protected network access technologies
- Microsoft Dynamics – intelligent business applications that deliver alerts and notifications via Microsoft Teams or Outlook
Vulnerability Types
Out of the list of vulnerabilities that have gotten patches, the following three vulnerabilities are known to be exploited in the wild:
CVE-2023-21715
The CVE-2023-21715 is a Security Feature Bypass Vulnerability in the Microsoft Office.
Microsoft Office is a suite of applications that helps with productivity and completing tasks on a computer.
The attack complexity is low, in order to exploit the vulnerability, the attacker requires a user to open a crafted file before the vulnerability can be exploited. The vulnerability allows an attacker to bypass Office macro policies that block untrusted or malicious files and execute code on a victim.
CVE-2023-23376
The CVE-2023-23376 is a 7.8 HIGH severity Privilege Escalation vulnerability in the Microsoft Windows Common Log File System (CLFS) Driver.
The Windows Common Log File System (CLFS) is a general-purpose logging service.
The attack complexity is low, the vulnerable system can be exploited without any interaction from any user and the attacker will gain SYSTEM privileges.
CVE-2023-21823
The CVE-2023-21823 is a Privilege Escalation vulnerability in the Microsoft Windows Graphic Component, the OneNote platform is known to be exploited.
The attack complexity is low, the vulnerable system can be exploited without any interaction from any user and the attacker will gain SYSTEM privileges.
Recommendations for February 2023 Patch Tuesday
We strongly recommend you take this patch seriously and install the patches immediately, with an emphasis on the vulnerabilities already known to be exploited in the wild.