Here’s What You Need to Know About the Confluence Vulnerability
By: Yotam Perkal, Director of Vulnerability Research, Rezilion
Cybersecurity firm Volexity has recently uncovered a zero-day vulnerability affecting all supported versions of Confluence Server and Confluence Data Center. The vulnerability, CVE-2022-26134, was identified during an incident response investigation of a couple of Internet-facing web servers running Atlassian Confluence Server software. On both hosts suspicious JSP web shells were observed being written to disk.
💡A web shell is a small piece of code, usually with malicious intent, which can allow an adversary to compromise web servers and launch additional attacks (privilege escalation, data theft, lateral movement and more). A webshell can be written in any typical web development programming language and is considered a comfortable attack tactic since its execution doesn’t require any additional programs and is not easy to detect.
A JSP web shell is simply a webshell written in JavaServer Pages (JSP).
Upon further analysis of the hosts, it was determined that the web shell files were related to an unauthenticated and remote OGNL injection vulnerability resulting in code execution in the context of the Confluence server (typically, on Linux installations, the confluence user).
💡 This is a good place to reiterate the fact that it is advised to avoid running any software as root without proper justification.
The vulnerability was acknowledged by Atlassian which consequently released the following security advisory.
In this blog post, we will highlight the main characteristics of the vulnerability as well as lay out suggested mitigation and remediation steps.
The Vulnerability
Similar to CVE-2018-11776, the Apache Struts2 namespace OGNL injection vulnerability, the vulnerability is caused by insufficient validation of user input stemming from Object-Graph Navigation Language (OGNL) expressions sent through crafted HTTP requests that are eventually evaluated and thus, potentially lead to remote code execution.
In plain english, an attacker can create a HTTP request which contains specific input which due to the faulty validation logic will be executed on the vulnerable server.
Later analysis conducted by Rapid7 has identified the root cause of the vulnerability in ActionChainResult.class and TextParseUtil.class. The patch has also introduced a new class called safeExpressionUtil.class which has been added to the existing OgnlValueStack.class and provides filtering of unsafe expressions.
Following the publication of the vulnerability, several exploit POCs have become available.The relative ease of exploitation, along with the fact that Confluence servers make for a high-value target have resulted in a constant uptick in active exploitation attempts.
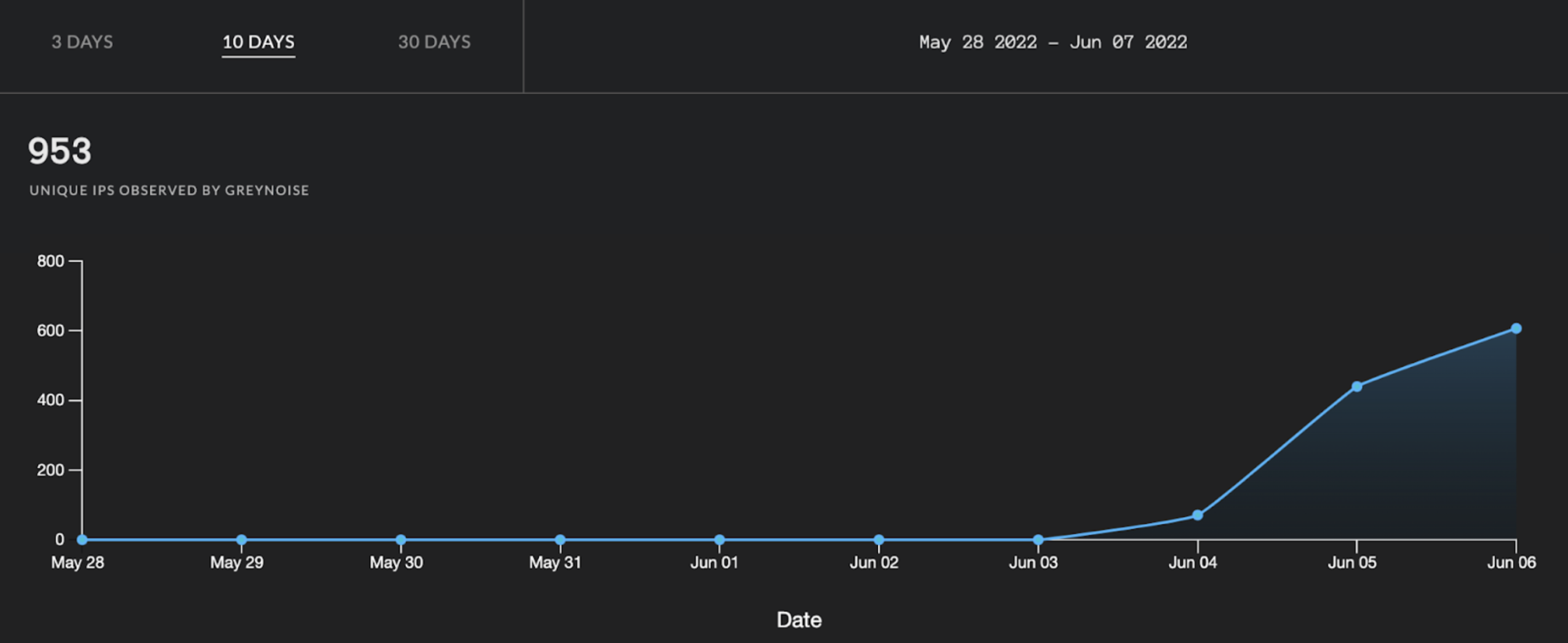
Currently, according to Greynoise, there are over 950 unique IP address observed trying to exploit the vulnerability:
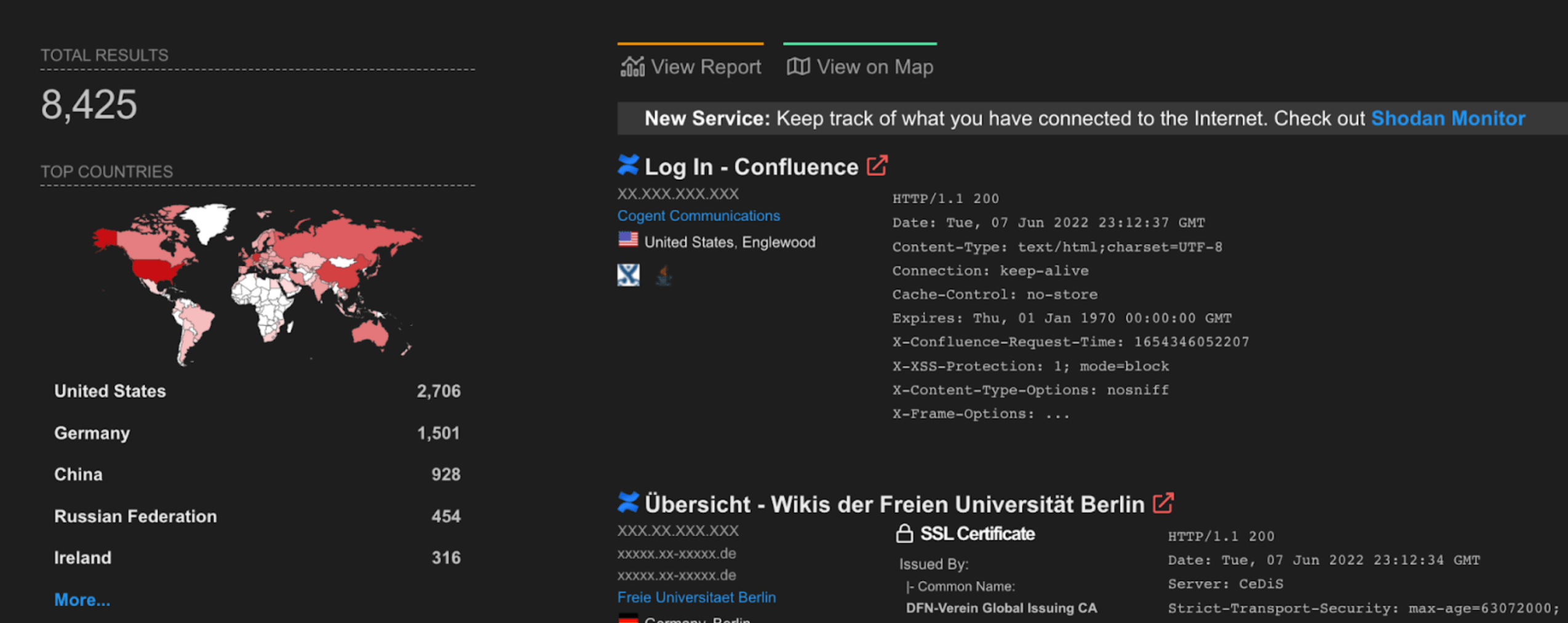
While Shodan Shows over 8400 interne-facing Confluence Servers:
Remediation
Atlassian has released the following fixed versions:
7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1
It is advised to upgrade to the latest Long-Term Support release (currently 7.18.1)
Note: On a Confluence cluster, this upgrade can not be performed without downtime.
Mitigation
If you are not able to upgrade Confluence immediately, according to the current guidance in the Attlasian security advisory, as a temporary workaround you can update specific files in order to mitigate CVE-2022-26134 (does not require downtime):
For Confluence Versions 7.15.0 – 7.18.0
- Shut down the confluence
- Download the following 1 file to the Confluence server: xwork-1.0.3-atlassian-10.jar
- Delete (or move the following JAR outside of the Confluence install directory): <confluence-installation-directory>/confluence/WEB-INF/lib/xwork-1.0.3-atlassian-8.jar (!Do not leave a copy of this old JAR in the directory!)
- Copy the downloaded xwork-1.0.3-atlassian-10.jar into: <confluence-installation-directory>/confluence/WEB-INF/lib/
- Check the permissions and ownership on the new xwork-1.0.3-atlassian-10.jar file matches the existing files in the same directory.
- Start Confluence
Note: if you are running Confluence in a cluster, you should apply the above update on all nodes.
For Confluence Versions 7.0.0 – 7.14.2
For these versions there are a couple of additional files that need to be installed:
• webwork-2.1.5-atlassian-4.jar (Should be placed in the Confluence installation directory.)
• CachedConfigurationProvider.class (Should be placed in the following path: <confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork)
Note: the webwork directory won’t exist and has to be created.
Note: if you are running Confluence in a cluster, you should apply the above update on all nodes.
Keep in mind that this mitigation was not fully tested for Confluence End Of Life versions.
If for any reason you are unable to remediate or mitigate the vulnerability, it is advised that you restrict or disable Confluence Server and Confluence Data Center instances immediately.