From 0 to Log4j Vulnerability Management: 3 Easy Steps in 3 Minutes

By: Baksheesh Singh Ghuman
Most enterprises, as well as small organizations globally are now painfully familiar with the Log4j2 vulnerability (CVE-2021-44228). It has taken over the lives of all cybersecurity professionals and it appears it is here to stay for a while. Most enterprises are scrambling for solutions, applying patches if they can find the vulnerability, and trying to implement mitigation strategies. But unfortunately what security teams are doing to tackle the Log4j beast is not always enough. Log4j is further complicated by four factors.
- First, the biggest challenge is finding your Log4j vulnerabilities. Log4j, due to its nesting nature, is hard to find. If you can’t see it, you can’t patch it or mitigate it.
- Second, the pervasive nature of Log4j makes it a large problem over an even larger attack surface – CI/CD pipeline, on-prem server, or cloud workload, network, etc.
- Third, there will be other attack vectors that will arise due to the vulnerability and if you can’t discover them, your problems are compounded. As we have already seen, the following mutations have already appeared:
a. A Remote code execution(RCE) vulnerability CVE-2021-45046 was found within CVE-2021-44228 was patched with Apache Log4j 2.16.0
b. CVE-2021-4104, also emerged, allowing RCE like CVE-2021-44228 and CVE-2021-45046 in certain non-default configurations
c. CVE-2021-45105, allows a Denial-of-Service (DoS) was patched with Apache Log4j 2.17.0 - Finally, there are not enough resources to combat this threat.
Log4j is a Mess, But it Doesn’t Have to Be
Rezilion Validate can help you manage your Log4j challenges in three easy steps that will take less than three minutes. Here is how.
Step 1: Create a Dynamic Software Bill of Materials (SBOM)
Within seconds, Rezilion Validate, through a continuous monitoring process, delivers a fully searchable, live, dynamic Software Bill of Materials. Unlike traditional scanning methodologies that are point-in-time or scheduled scans, dynamic SBOMs are continuously updating and thus provide you a real time view into the different components and drift associated with them.
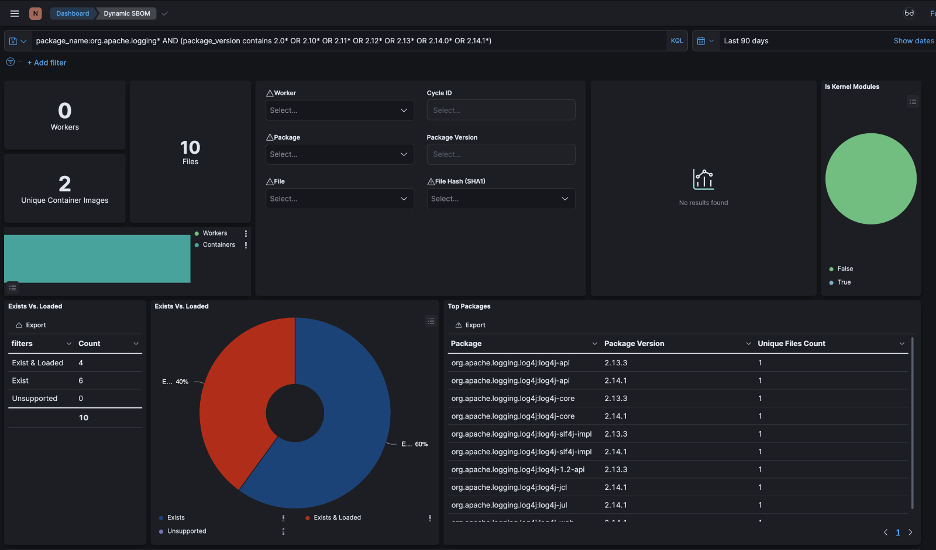
This dynamic SBOM is a key first step to discovering your Log4j vulnerabilities. The following series of screenshots shows you how easy it is to discover your Log4j vulnerabilities using Rezilion Validate.
Figure 1: Rezilion Validate main dashboard
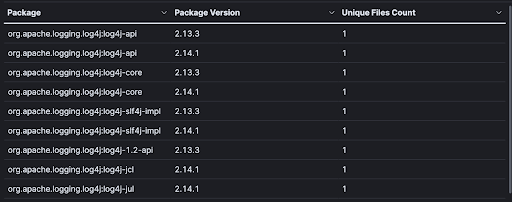
Figure 2: Zoomed view of all Log4j packages discovered
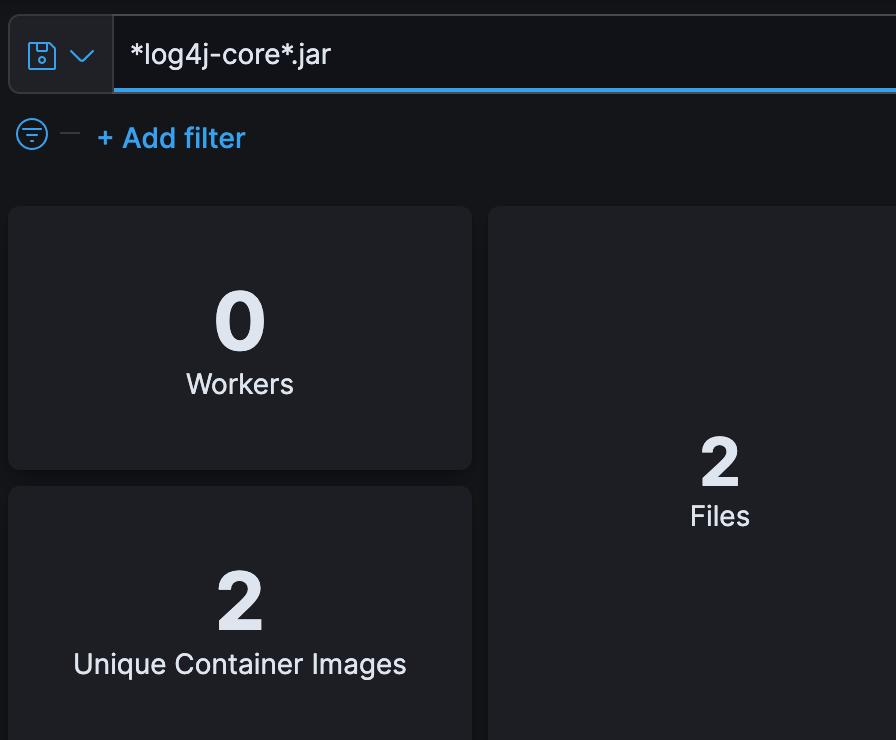
Figure 3: Searchable, dynamic SBOM
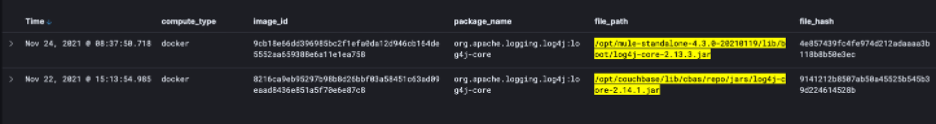
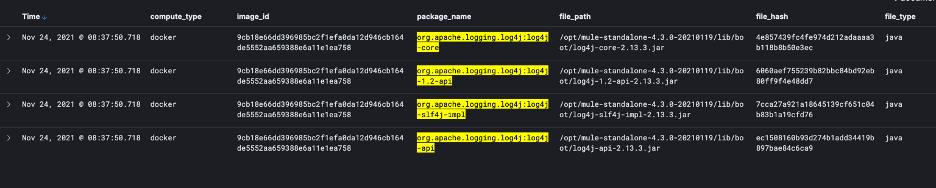
Figure 4: Search Results of specific Log4j files/packages
As you can see, it is quite easy to discover Log4j packages/files, whether nested or un-nested, using Rezilion Validate. Once you have discovered all the Log4j packages in your environment, the next step is to find out if they actually pose a threat to your environment.
Step 2: Establish Exploitability Context
Just because you discover Log4j packages within your environment, it does not mean that your environment is vulnerable. The instances have to be exploitable. Rezilion Validate’s proprietary mining technology established the exploitability context. Our mining technology informs us of the packages/files that are loaded into the host’s or particular device’s memory. This is where Rezilion provides value to our customers – with the ability to only focus on what is exploitable and not every single vulnerability that is discovered.
Once we understand what is running in the host’s memory, content is then mapped back to the originating source on each file system, allowing linkage between memory and files, packages, libraries, JARs (nested or otherwise), etc. This association is quite powerful as it establishes the context necessary to determine exploitability of a vulnerability.
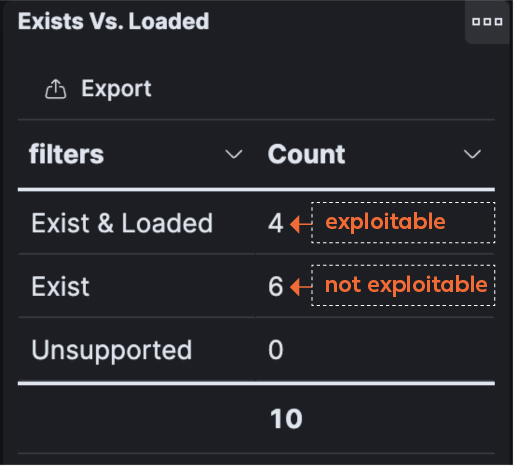
Figure 5 below illustrates my point. It shows that there are 10 packages that contain the Log4j vulnerability, but only four are “loaded”. Translation: only 4 are exploitable. That makes a big difference when you have hundreds or even thousands of vulnerabilities.
Figure 5: Exploitable or not
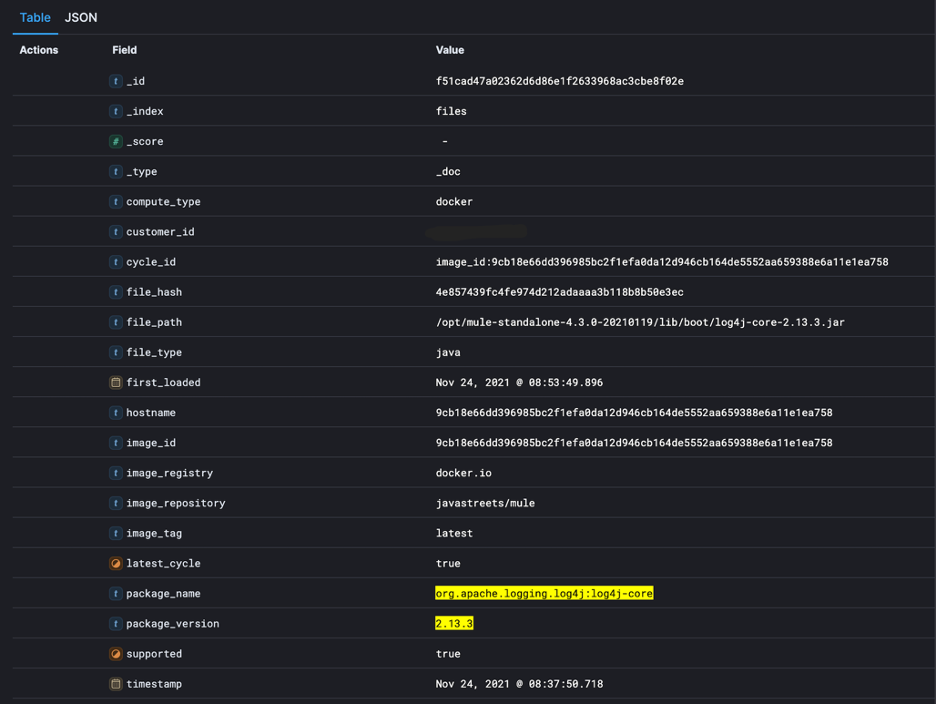
Figure 6: Detailed information about each loaded package
Step 3: Remediate
Now that you know what is exploitable in your environment, it is time to take action against them. After filtering out the six that are not loaded into memory, Rezilion Validate creates a detailed risk report on assets that are exploitable, with clear remediation guidance allowing for practitioners to focus their remediation efforts on what matters the most.
This approach to remediation has worked for our customers in reducing their patching efforts by 70%, decreased their remediation timelines from months to days, and allows them to quickly focus on critical vulnerabilities that pose a threat to their environment.
Log4j: It Can Nest, But it Cannot Hide
Our proprietary approach to software attack surface management that is powered by our dynamic SBOM and vulnerability contextualizing methodology offers a powerful tool for cybersecurity practitioners and managers to discover, mitigate, and remediate vulnerabilities like Log4j as well as increase their security posture.
Sound easy? It does because it is. Rezilion Validate is designed with a simple philosophy – help customers validate what is exploitable.
If you are interested in finding out how Rezilion can help you with managing your Log4j vulnerability challenges, please schedule a Log4j risk assessment with us today. Learn more about Rezilion Validate.