
Dynamic SBOM = SBOM + VEX

In recent months there has been a lot of discussion around the importance of Software Bills of Materials (SBOM) and Vulnerability Exploitability Exchange (VEX) when it comes to managing software vulnerabilities.
Organizations can combine the SBOM and VEX to get a more contextualized view of the actual risk present in their environment. In this blog post, we examine how SBOMs and VEX do not need to be 2 artifacts. Instead, organizations can use a Dynamic SBOM that combines a real-time SBOM and the VEX.
How to Generate an SBOM with Context
A Software Bill of Materials, or SBOM, is a machine-readable artifact that is an inventory of all software components present in the software. The goal of SBOMs is to provide greater transparency on the composition of software, its dependencies, provenance, and the potential risk associated with such components. However, today’s SBOMs have some limitations.
- Today’s SBOMs are static
- SBOMs are not fully automated
- SBOMs are specific to certain software or applications
- SBOMs require an additional artifact for context
- Current SBOM outputs are very large and noisy
SBOMs are useful tools to achieve visibility into all of the software components at different stages of the DevOps lifecycle, from development to production. Once you have the entire list of components, it is important to know which of these components are vulnerable and which one needs to be prioritized and fixed. In order to do so effectively, organizations need contextual information on which vulnerabilities are exploitable in their environment and which ones don’t pose a risk. This is where the VEX comes in.
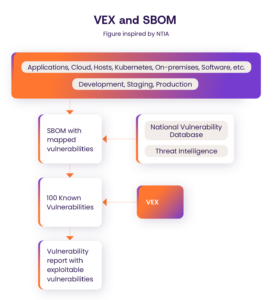
Figure 1
VEX: Insights Into What is Exploitable
VEX is a machine-readable artifact that tells you which vulnerable components in an environment are actually exploitable. The objective of the VEX is to provide information for organizations to use and prioritize their remediation efforts.. This contextualization is provided by the software vendor with a machine-readable artifact with justification values of why a particular component is not affected by a specific vulnerability and therefore not exploitable.
Figure 1 illustrates how organizations can take advantage of VEX. By using a VEX organizations can reduce their total number of vulnerabilities and focus on vulnerabilities that need to be remediated immediately, as they pose the most risk in a specific environment.
Do I Need to Create an SBOM and VEX Separately?
In order to truly understand what is exploitable or not, an organization needs two artifacts – an SBOM and a VEX -which have to be updated and created every time there is a change in the software. This is a cumbersome and manual process, not one that can be sustained or scaled. The answer to this dilemma is a dynamic SBOM. Let’s find out why.
Dynamic SBOMs are Continuous
- SBOM reflects changes as your environment changes
- No need to maintain multiple versions
- Offers continuous risk assessment
End to End- Full Stack/Full Cycle and Comprehensive
- Provides visibility into your entire software environment from dev to production
- Covers a broad range of software component types such as containers, applications, hosts, packages, and files.
Searchable and Customizable Results
- Customize using filters to define acceptable risk thresholds
- Search by every identifier of the component
- Drill down
Contextualized
- VEX – built-in the dashboard as well exportable as a separate artifact.
- Provides context on what is exploitable or not exploitable in your environment and reveals what is loaded or not loaded to memory.
- Run time context tells you where to focus your remediation efforts
Automated and scalable
Dynamic SBOM = SBOM + VEX
When using a Dynamic SBOM, organizations don’t need two documents to know which components are not exploitable, they can get a single automated and continuous dashboard that updates and scales with the software while providing dynamic insight into the risk associated with an organization’s software environment. This information enables developers and product security teams to release certain products quickly. Figure 2 illustrates how this blended Dynamic SBOM and VEX approach reduces the vulnerability backlog by up to 85%. Some of the benefits of using a Dynamic SBOM with embedded VEX are
End-to-end view of the entire software environment from development to production.
Quick understanding of the true attack surface by focusing on vulnerabilities that are exploitable.
Prioritization for easy remediation.
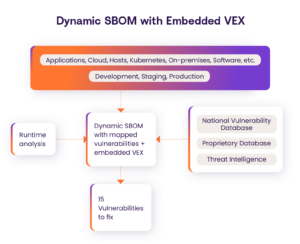
Figure 2
Rezilion’s Dynamic SBOM is available now, free-of-charge for use, in CI environments such as Jenkins and Gitlab. You can read more on VEX at https://www.rezilion.com/lp/all-about-the-vulnerability-exploitability-exchange-lets-talk-about-vex/
For more information, visit https://www.rezilion.com/platform/dynamic-sbom/ and to sign up for a free 30-day trial at https://www.rezilion.com/book-demo/.




