Critical PaperCut Vulnerability CVE-2023-27350 Exploited by Threat Actors

In this blog post, we detail PaperCut Vulnerability CVE-2023-27350. On March 8th, PaperCut released new versions that contained security updates and addressed two recently discovered CVEs – CVE-2023-27351 and CVE-2023-27350.
Today, we will focus on CVE-2023-27350, which was reported by the Zero Day Initiative (ZDI-23-233). This vulnerability is a critical remote code execution flaw with a severity score of 9.8. It affects PaperCut NG and PaperCut MF, and is currently being exploited by threat actors. It is recommended that affected systems be patched immediately by updating to one of the following versions: 20.1.7, 21.2.11, or 22.0.9.
What is PaperCut?
PaperCut is a print management software that helps organizations manage their printing environments. It provides features such as print job tracking, quotas, rules-based printing, and cost accounting. The software can be used to monitor and control printing activity, set printing policies, and generate reports on printing usage and costs. PaperCut can be deployed on-premise or in the cloud and supports a wide range of printers and operating systems. The software is used by organizations of all sizes, including schools, universities, government agencies, and businesses.
More on PaperCut Vulnerability CVE-2023-27350
The vulnerability identified in the PaperCut software stems from an access control issue within the SetupCompleted java class in the pcng-server-web jar file.
The vulnerability found is a Session Variable Overloading vulnerability (aka session puzzling).
Session Variable Overloading
The Session Variable Overloading vulnerability arises when an application assigns the same session variable, such as “userid,” with the user’s username upon login, and subsequently uses this variable in database queries to retrieve user-specific data. However, the application does not perform additional checks to ensure that the user is authenticated and authorized to access the requested resources.
Breakdown of the vulnerability:
- Upon login, the application creates a session variable called “userid” and sets its value to the username of the logged-in user.
- Throughout the application, SELECT queries are executed using the “userid” session variable to retrieve data specific to the authenticated user.
- However, the application neglects to verify if the user is truly authenticated and authorized before processing the queries.
- Exploiting this vulnerability, an attacker can manipulate the session variable, tricking the application into displaying or granting access to unauthorized user-specific data.
In CVE-2023-27350, the SetupCompleted class has a function called formSubmit which is called when submitting a form. This function calls the getSetupData function without confirming that the user is logged in and then calls the performLogin function with Admin permissions. Since the user is not confirmed to be logged in, an attacker can easily bypass the authentication and access the page with admin permissions.
After successfully bypassing the authentication, the attacker can create scripts in the PaperCut application that execute code, if the attacker executing (in windows for example) cmd.exe or powershell.exe, these processes will be created under the PaperCut process – pc-app.exe, which is executed with SYSTEM privileges, result in a remote attacker executing code with SYSTEM privileges on the affected PaperCut server.
The Fix for PaperCut Vulnerability CVE-2023-27350
The recommended fix for the Session Variable Overloading vulnerability is to basically add a check to see if the user is authenticated before performing queries.
The fix PaperCut applied is the same, before calling the performLogin function with admin permissions, they now call the getSetupData function with the isConfirmed function to validate the user is logged in (was authenticated). If the code finds that the user is not authenticated, it sends him back to the Home web page.
PaperCut Vulnerability CVE-2023-27350 in the Wild
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have jointly released an advisory regarding the active exploitation of CVE-2023-27350 by threat actors. According to the FBI, threat actors have been exploiting this vulnerability since mid-April and continue to do so. Recently, in early May 2023, the Bl00dy Ransomware Gang targeted vulnerable PaperCut servers used in the Education Facilities Subsector that were exposed to the internet. The exploitation led to data exfiltration and encryption of victim systems, with ransom notes demanding payment in exchange for the decryption of encrypted files.
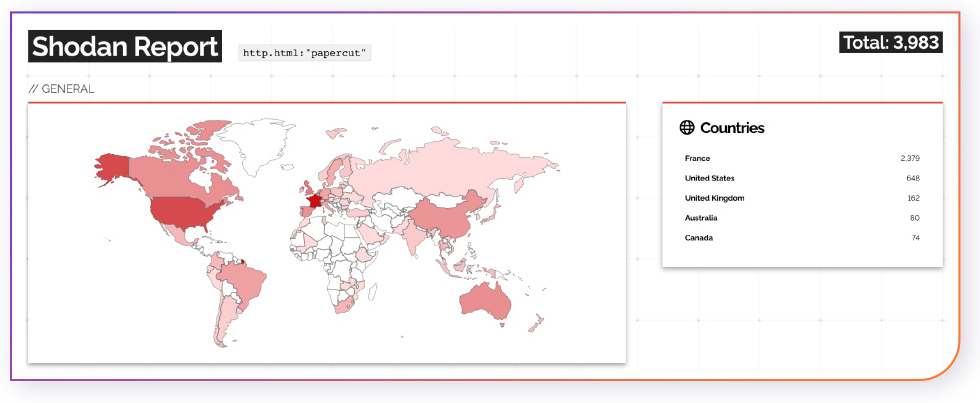
Based on data from Shodan.io, there are currently 3,983 PaperCut hosts that are exposed to the internet and may be vulnerable to the CVE-2023-27350 exploit.
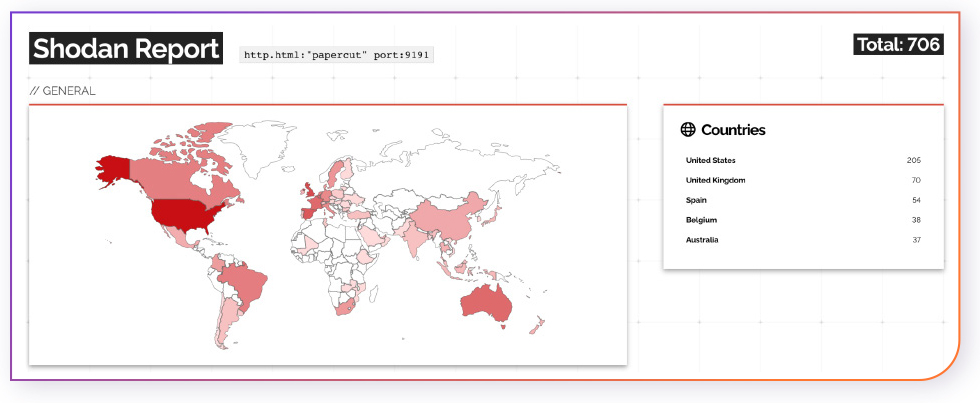
Since port 9191 is the default port used for accessing the PaperCut web administration interface, we examined how many PaperCut hosts with port 9191 open are exposed to the internet and there are 706.
It is important to note that we can not find the PaperCut product versions via Shodan output so the numbers of the PaperCut hosts means they are susceptible to CVE-2023-27350 but there is a need for a version check in order to determine they are exploitable.
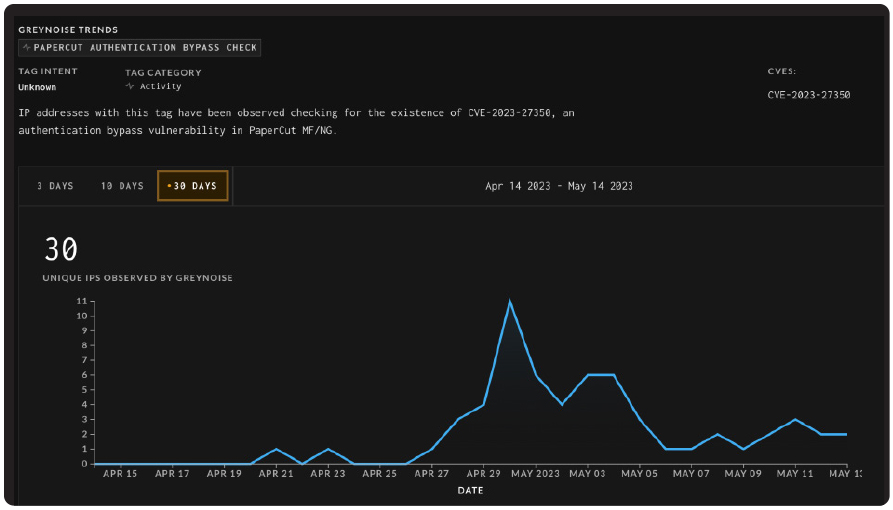
According to GreyNoise, there have been 30 checks for the existence of CVE-2023-27350 in the last 30 days.
POCs exploiting the vulnerability were published to the public.
Exploit Details for PaperCut Vulnerability
The second POC is a Python script that performs a vulnerability scan for CVE-2023-27350 on a PaperCut server by checking the version number of the software and bypassing the authentication.
The following exploit method searches in the html searches for a <div> element with class text and a <span> element with class product, which should contain information about the PaperCut product.
Versions need to meet the following regular expression pattern: ^\d+\.\d+\.\d+$, that start and end with the version which has 3 ocatate of digits.
If a version number is found, the function prints the version number, the HTTP status code of the response, and two URLs to visit for further testing: one to the setup completed page: http://<ip>:9191/app?service=page/SetupCompleted and the other to the dashboard page: http://<ip>:9191/app?service=page/Dashboard, which is accessed without authentication.
The second POC, is a Python script that exploits the CVE-2023-27350 vulnerability in the PaperCut printing system, it performs both bypassing authentication and the RCE. It works by taking a PaperCut application URL and a command to execute as input from the user. The script first performs a GET request to the <url>/app?service=page/SetupCompleted and then performs a POST request to the URL to try to login and get a valid cookie. If the response is a 200 status and contains the string “papercut” and a valid JSESSIONID cookie, the function returns the requests, otherwise, it returns None. If the login is successful, the exploit tries to enable/disable certain PaperCut settings required for the code execution. It sets two parameters to the desired settings and performs some GET requests to specific pages to find an existing printer. Then, it reaches the PrinterDetails page where it sets up a print job hook and executes the inserted command by user using the java.lang.Runtime.getRuntime().exec('{command}') command. If the response is a 200 status and contains the string “Saved successfully”, then the exploit worked successfully.
Affected PaperCut Versions
The first version in each range is affected by the vulnerability and the second version in each version is patched – not affected.
PaperCut MF/ PaperCut NG – 8.0.0 through 20.1.7
PaperCut MF/ PaperCut NG – 21.0.0 through 21.2.11
PaperCut MF/ PaperCut NG – 22.0.0 through 22.0.9
Recommendations
Since this vulnerability is actively exploited in the wild, we advise defenders to assume compromise and look for any abnormal activity that could be associated with exploitation attempts.
More guidelines and updates can be found in the CISA and FBI advisory.
Remediations
If you have the affected versions listed above of PaperCut MF/NG make sure to patch immediately to one of the following versions: 20.1.7, 21.2.11, 22.0.9.
Mitigations
If for any reason you are unable to patch, make sure your vulnerable servers are not exposed to the internet.
Detect and Incident Response
Monitor network access to SetupCompleted pages of vulnerable PaperCut instances, Try to identify child processes stemming from the pc-app.exe PaperCut process and monitor system logs for any indication of malicious activity, specifically focusing on PaperCut server’s settings and log files.